Understanding BotBasher's Biometric Privacy and Security Approach
Following the tremendous success of BotBasher's official beta launch, multiple users have voiced concerns about data processing and privacy. These users have posed several critical questions that they want us to explore and answer: How does BotBasher ensure the security and privacy of data during the biometric verification process? What measures are implemented to safeguard users' personal information? Are there potential risks associated with storing biometric data, and if so, how does BotBasher mitigate these risks?
In this article, we'll address these considerations, providing an in-depth look at how BotBasher processes and protects user data through Confidential Computing technology.
We'll discuss the various stages of Humanode’s biometric verification process, from data collection to encryption and storage, and explore how BotBasher prioritizes user privacy and security at every step.
The aim is to alleviate your concerns and demystify the world of data protection in BotBasher. So let’s delve into it.
Humanode’s Verification Process
BotBasher's biometric verification process comprises several stages to verify that a user is a unique living human. Let’s discuss each step individually and find out how users’ data is shielded from potential attacks at every step.
-- Data Collection: To verify that a user is a living human being, they have to go through a live video-based 3D face scan using any device with a camera of at least 3 megapixels. It is a 10-15 seconds process. During this process, the platform's neural network transforms the video feed into an anonymized 3D template simultaneously verifying liveness.
-- Encryption and Transmission: The anonymized 3D template and liveness data are encrypted using asymmetric cryptography while still on the user’s device and sent over the network to the Confidential Virtual Machines(VMs).
-- Data verification: This process is very critical as there is a potential for attacks happening at this stage. The encrypted data arrives on Confidential VMs that utilize AMD SEV-SNP. AMD SEV-SNP provides hardware-based encryption to safeguard the entire VM from unauthorized access, including potential intrusion by the host administrator. The protection extends to the hypervisor, which is managed by the cloud service provider (CSP). This ensures the prevention of any physical attacks by host admins as well as state-backed attacks.
For example, what if the FBI raids one of the locations where these servers are located? In the case of normal Confidential Computing operations, someone with physical access can get their hands on the components of servers using multiple tactics but in servers utilizing AMD SEV-SNP, this is not possible.
While AMD SEV-SNP effectively mitigates the risk of physical attacks, there is another type of threat to consider: attacks by super administrators, or in simpler terms, those who set up the servers. In the case of BotBasher, this refers to us.
To address this concern, SEV-SNP technology provides an option to configure it in a way that even the super admins do not get access to the components of data on the server.
Technically, while configuring the server, we upload our initial image. This initial image contains the guest VM code. At the end of the launch process, we send the signed identity block (IDB) containing the launch digest to VM. The contents of this identity block allow the guest owners to uniquely identify the VM. VM then asks SEV-SNP firmware for an attestation report. The attestation report contains IDB and the launch digest. The core purpose of this process is to verify and authenticate the VMs hardware and launch digest.
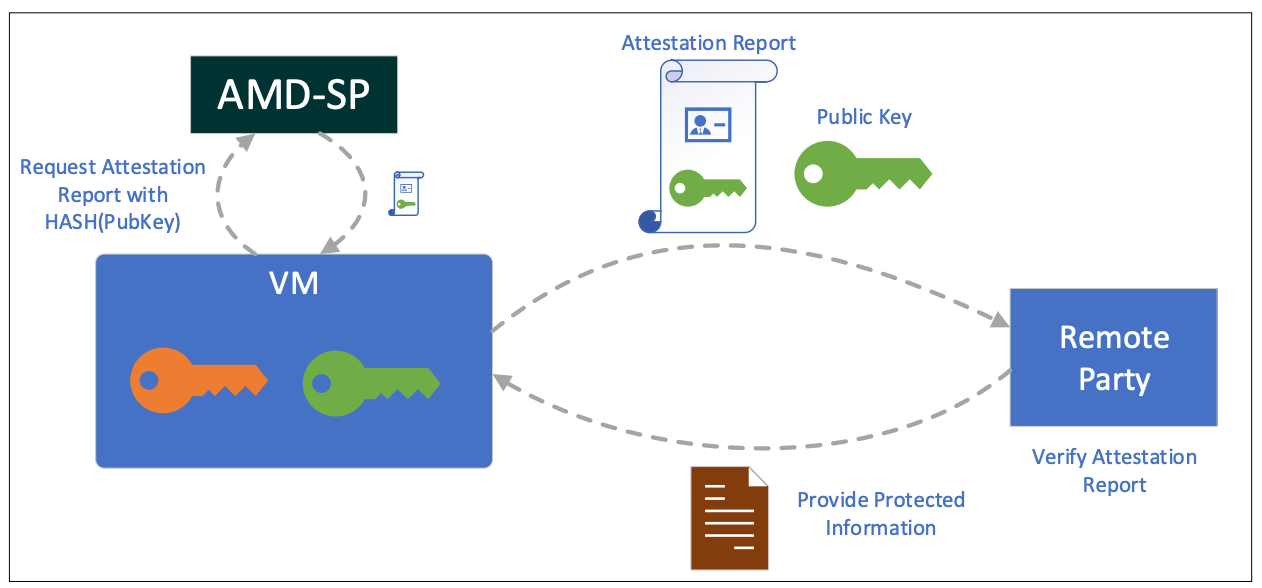
When we configure Confidential VMs, it’s done in a manner that prevents our access. We do not possess any passwords or SSH keys to access the VM. Instead, we prepare a suite of software in a way that, upon boot, self-configures and independently generates all necessary keys.
In Layman’s terms, we use Confidential Computing VMs utilizing AMD SEV-SNP to boot servers in such a way after launching, it self-configures and self-executes to process and store the data in an encrypted form so that no one, not even we, can access or temper the data in any stage of the data-life cycle be it data in use, data in transit or data at rest.
For users to get verified, two components are required: an anonymized 3D face template and liveness data. The Confidential Computing servers compare the newly arrived encrypted and anonymized 3D face templates against those already registered in the system in such a way that before sending the already encrypted data to memory for processing, it is encrypted again for protection from physical attacks.
As for the liveness data, it is timestamped and immediately deleted after verifying that the user is an actual live human being, not a facemask, photograph, or a deep fake.
-- Data storage: Once the data is authenticated, the encrypted and anonymized 3D face template is saved on the Confidential virtual machine (VM), and a random string is generated, which is linked to the Discord ID.
Since the liveness data gets deleted immediately and only a random string associated with Discord ID is stored, even if an attacker gains access to servers, the only information they could potentially retrieve is a Discord ID associated with a random string, rendering the data useless for malicious purposes.
In summary, the safeguarding and privacy of biometric data are paramount in our technology. From the outset of the data collection process, we ensure that no data can be traced back to a specific user by anonymizing the 3D face templates. By employing confidential computing, we guarantee that data is never transmitted without encryption. Moreover, through the use of AMD SEV-SNP, we make certain that the data remains inaccessible to anyone at any stage of the data lifecycle.
We hope this article has answered your inquisitive questions about data privacy and protection in BotBasher. Using Confidential Computing technology, AMD SEV-SNP, and robust data protection practices, BotBasher ensures that users can enjoy a seamless and secure experience without compromising their personal information.

