One Pass to Rule Them All – A comparison between SRGATE and other Login solutions

Imagine waking up to find your online identity hijacked, your social media profiles, email accounts, and even your bank details compromised. In 2024, such scenarios became alarmingly common, with over 1.1 million identity theft reports filed through the FTC's IdentityTheft.gov platform. And that’s just the tip of the iceberg.
The digital landscape is teeming with fake accounts and bots. Facebook alone removed approximately 1.1 billion fake accounts in the third quarter of 2024. These inauthentic profiles are not just numbers; they are tools for spreading misinformation, conducting scams, and undermining trust in online interactions. Even it doesn’t end there. Tried managing passwords for every app?
As of early 2025, the average internet user manages nearly 170 passwords, a significant increase from previous years. This proliferation of credentials not only burdens users but also creates vulnerabilities, as many resort to reusing passwords across multiple platforms.
Login with Google might save you time, but it also hands over the keys to your digital life. These login buttons are more than just shortcuts, they’re access passes to your identity, controlled by a handful of companies.
If one decides to suspend your account, change their policies, or get breached? You’re locked out. Worse, your login data becomes part of a sprawling surveillance economy, monetized and repackaged by algorithms you’ll never meet. And that has kept happening in the past.
And there’s another layer most people don’t see: these systems don’t stop people from creating 10, 100, or 10,000 fake accounts. There’s no real uniqueness check, just a working email, maybe a phone number. That’s how botnets and Sybil attacks slip through the cracks and flood platforms with spam, manipulation, and fraud. Centralized logins may know who you are (kind of), but they don’t know if there are a hundred yous gaming the system.
Now combine all that with the rise of deepfakes and autonomous AI agents that can generate realistic video, voices, and even full-blown online personas, sowing confusion and faking legitimacy. Suddenly, proving that you’re you online isn’t just about security, it’s about survival in a digital world where bots can do everything a human can, and often smarter and faster.
So we’re left with the obvious question:
Can we build a better login?
- One that works everywhere, but doesn’t spy on you.
- One that proves you’re human, but doesn’t reveal who you are.
- One that you actually control.
That’s the vision driving a new generation of identity systems, from Big Tech’s familiar offerings to blockchain-native experiments like Gitcoin Passport, BrightID, and the upcoming SRGate by Humanode.
So, where does that leave us?
We’ve seen the cracks in the current system, centralized logins that know everything about you but can’t tell if you’re real, botnets running wild, and also having control over your data, adding to that, AI personas flooding our feeds. We don’t just need a better login – we need a different kind of login altogether.
But before we dive into all the contenders – from Big Tech to blockchain – let’s break down what a global, human-first login should actually look like. What would it take to create a login that works everywhere, proves you’re human, respects your privacy, and gives you full control?
Here’s what we’re really looking for.
What Makes a True Global Login Solution?
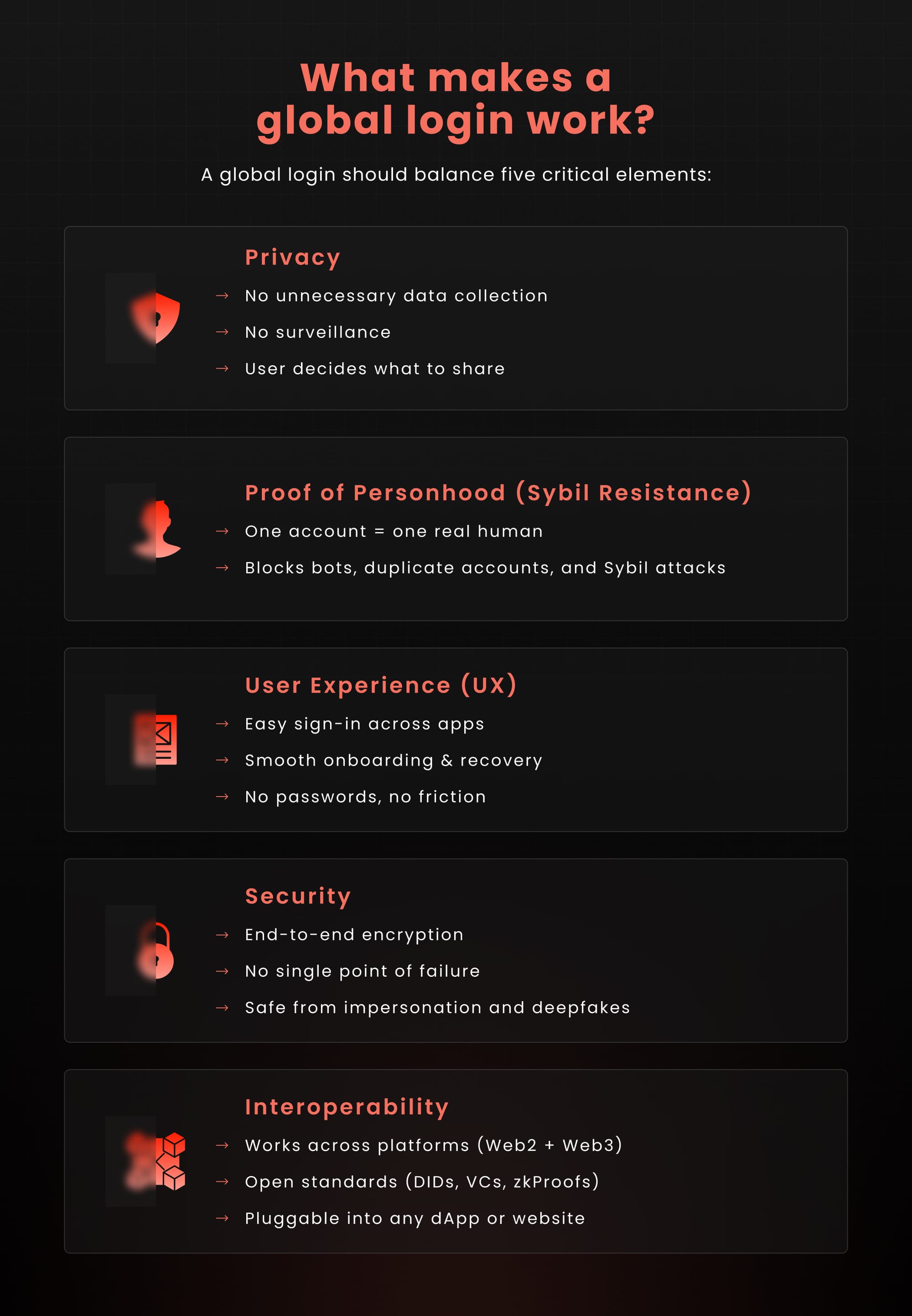
In an ideal digital world, logging into any platform – be it a social media site, an e-commerce store, or a decentralized application, would be seamless, secure, and respect user privacy. However, achieving such a universal login system involves balancing several critical factors:
1. User Control and Privacy
Back in 2021, Tim Berners-Lee, the creator of the world wide web itself, described the current system as broken. His project, Solid, pushes for users to own their own data and choose where and how it’s shared. “The web was meant to serve humanity,” he said, “not become a tool for surveillance capitalism.”
Jack Dorsey, former Twitter CEO, has echoed that. He's publicly pushed for self-sovereign identity as part of a more decentralized internet stack, where no single platform holds your online credentials hostage.
Centralized login systems often require users to surrender personal data, which is then stored on centralized servers. This not only raises privacy concerns but also creates attractive targets for cyberattacks.
In contrast, decentralized identity solutions empower users to control their data, sharing only what's necessary. For instance, decentralized identifiers (DIDs) allow individuals to prove aspects of their identity without revealing unnecessary personal information. SlashdotDock Labs - Decentralized ID Management
2. Sybil Resistance
A significant challenge in digital identity is ensuring that each individual has only one identity within a system, preventing Sybil attacks. Vitalik Buterin has written extensively about the need for proof of personhood as a base layer for governance, voting, and identity online.Centralized systems often lack robust mechanisms to prevent such attacks.
Decentralized systems, however, can employ techniques like social graph analysis or biometric verification to enhance Sybil resistance. Dock Labs - Decentralized ID Management
3. Interoperability Across Platforms
Elon Musk might not be the poster child for privacy, but even he recognizes the importance of a single identity that works across systems. His plans for “X as the everything app” include verified logins, payment systems, and communications, essentially, a federated ID under his platform. It's the centralization we’re trying to avoid, but it shows that the demand for a universal login is very real.
A true global login should work seamlessly across various platforms and services. This requires adherence to open standards and protocols that ensure compatibility. Decentralized identity systems often leverage standards like W3C's Verifiable Credentials and Decentralized Identifiers to promote interoperability. MDPI+4Dock Labs - Decentralized ID Management+4DEV Community+4
4. Security and Resilience
Centralized systems present single points of failure; if the central server is compromised, all associated identities are at risk. A breach at Facebook, Google, or Apple potentially exposes millions. A truly global login should be verifiable, encrypted, and decentralized.
Vitalik and others have pointed out that zero-knowledge proofs, biometric attestation, and secure enclaves could be the building blocks for this kind of tamper-proof authentication layer.
5. User Experience and Accessibility
Let’s be honest, no matter how secure or private it is, if it’s not easy to use, people won’t switch. That’s the real edge centralized systems still have. One click. No friction.
For decentralized or hybrid systems to compete, onboarding has to be just as smooth, with good account recovery, mobile support, and developer integrations. Anything less, and users will stick with what they know.
In summary, creating a universal login system that is secure, private, and user-centric requires a shift from traditional centralized models to decentralized frameworks. By addressing challenges like Sybil resistance, interoperability, and user experience, decentralized identity solutions hold the promise of redefining how we authenticate ourselves online.
Next, we'll explore the landscape of centralized Login systems, examining their strengths and limitations in the quest for a global login solution.
The Centralized Giants: Google, Apple, Facebook
In the quest for a universal login, centralized platforms like Google, Apple, and Facebook have long dominated the landscape. Their single sign-on (SSO) solutions offer convenience, but they come with their own sets of challenges and considerations.
Google Account: Convenience at a Cost
Google's SSO is ubiquitous, allowing users to access a multitude of services with a single click. However, this convenience often requires sharing personal information such as your name, email address, and profile picture with third-party apps . While Google emphasizes user consent and data security, the centralized nature of its system means that a breach or policy change can have widespread implications. Privacy Guides Community
Apple ID: Privacy-Focused, Yet Not Fully Open
Apple's "Sign in with Apple" aims to prioritize user privacy. Features like "Hide My Email" allow users to mask their email addresses, and Apple claims not to track users' app interactions. However, Apple's ecosystem is tightly controlled, and while it offers enhanced privacy, it doesn't fully embrace the open standards that promote interoperability across diverse platforms.
Facebook: Battling Fake Accounts
Facebook has faced significant challenges with fake accounts. In the third quarter of 2024 alone, the platform removed approximately 1.1 billion fake accounts . This highlights the platform's ongoing struggle with Sybil attacks and the difficulty of ensuring that each user represents a unique individual.
While centralized login systems offer ease of use, they often fall short in areas like user control, privacy, and resistance to fraudulent activities.
As we explore decentralized alternatives, it's essential to consider how these systems address the limitations inherent in centralized models.
Deep Dive into the Leading Decentralized Login Solutions
We started with a question: Can we build one login that works across the web, respects privacy, and proves you're human?
So far, we’ve looked at the need for a new kind of login. One that doesn’t hand over your life to Big Tech, doesn’t get gamed by bots, and doesn’t make you verify your identity 47 times across 47 platforms.
Now let’s look at the tools trying to solve that. Some are Web2-ish with Web3 flair. Some are full-on decentralized experiments. Others are biometric, social, cryptographic, or all of the above. But each one offers a different path toward the same goal: proving you’re a real person, not a Sybil, without turning your online life into a police report.
Here’s a deep dive into the most talked-about platforms:
1. Worldcoin
Worldcoin is bold: scan your iris, get a unique ID, maybe some tokens. The infamous Orb (available in 35+ countries) captures your iris pattern, converts it to a hash, and checks whether it already exists on the network. If it doesn’t, you get a World ID.
Worldcoin’s vision is a global digital passport for humans, with uses ranging from Sybil-resistant voting to UBI distribution. It’s biometric, it's ambitious, and yes, it’s controversial. The biggest plus? Near-perfect Sybil resistance. The biggest downside? It requires trusting a globe-spanning fleet of Orbs and a company still working toward full decentralization.
Strengths:
- High biometric accuracy.
- Enables global UBI, Sybil-resistant governance, fair airdrops.
- Zero-knowledge privacy improvements via secure multi-party computation.
Limitations:
- Centralized hardware and rollout.
- Limited Orb availability.
- Regulatory backlash and ethical concerns.
Technical flavor: Cryptographic iris hashes, secure multi-party computation, open-source Orb software (in progress), biometric uniqueness without storing actual biometric images.
2. BrightID
BrightID takes a very different route: no biometrics, no KYC. It proves you’re a unique person based on your social graph. You download the app, scan QR codes with people you meet, and build a web of trust. The algorithm analyzes how you’re connected to others to determine if you’re likely unique.
It’s perfect for communities and privacy diehards. The upside: no real-world identity required. The downside: onboarding friction. If you’re not already connected to someone verified, the path to verification can be slow.
Strengths:
- Fully decentralized, no KYC or biometrics.
- Composable across chains and apps.
- Privacy-preserving and open-source.
Limitations:
- Onboarding can be difficult for newcomers.
- Vulnerable to collusion in sparse graphs.
- Slower to scale due to network effect reliance.
Technical flavor: Graph-based uniqueness detection, peer-to-peer connections, BrightDAO governance, open-source infrastructure.
3. Proof of Humanity (PoH)
PoH combines a video selfie, vouching by another verified human, and a public registry of humans maintained on-chain. It’s one of the few systems that combines social validation with visible identity, and it powers things like UBI distributions and DAO voting.
The good: decentralized, transparent, and democratic. The challenge? It has serious privacy tradeoffs, you post your face on IPFS for everyone to see. And it’s vulnerable to forks, drama, and governance turbulence (as recent events have shown).
Strengths:
- Transparent, public registry.
- Community-driven dispute resolution.
- Incentivized correctness via UBI and challenges.
Limitations:
- Publicly exposes user faces (privacy tradeoff).
- Long challenge periods and onboarding friction.
- History of forks and governance turbulence.
Technical flavor: Smart contracts on Gnosis Chain, Kleros decentralized arbitration, video-based Sybil resistance, community challenge periods.
4. Gitcoin Passport
Instead of betting on one method, Gitcoin Passport aggregates many. It collects “stamps” from your accounts (Twitter, GitHub, ENS, BrightID, PoH, etc.), assigns weights, and gives you a trust score. Projects can use your Passport score to determine whether you qualify for airdrops, grants, or platform access.
Great for flexibility and real-world use. But it still leans on centralized credentials (Twitter, Google), and its scoring algorithm is still evolving.
Strengths:
- Easy to plug into existing dApps.
- Flexible, privacy-preserving trust model.
- Supports both Web2 and Web3 credentials.
Limitations:
- Still depends on centralized platforms (e.g., Twitter).
- Doesn’t enforce strict one-human-one-ID.
- Weights and scoring are still evolving.
Technical flavor: Decentralized Identifiers (DIDs), Ethereum Attestation Service, Ceramic network (optional), composable identity credentials.
5. Idena
Idena is weird. In a good way. It’s a blockchain where consensus is built on proof-of-personhood: every node equals a human who solves AI-resistant CAPTCHAs at the same time globally. You solve puzzles (called Flips), others solve yours, and if you pass, you’re in.
It’s one of the few systems where your identity is proven not by who you are, but by what you can do, show up and solve puzzles like a human, not a bot. The result? Egalitarian consensus. The cost? You have to be online for global validation sessions at sometimes weird hours.
Strengths:
- Egalitarian consensus, one human, one vote.
- No personal data or KYC.
- Resists automation and bots via AI-hard CAPTCHAs.
Limitations:
- Requires attendance at fixed global validation times.
- Limited integrations outside its native chain.
- UX and the learning curve can be rough.
Technical flavor: Peer-to-peer CAPTCHAs, decentralized consensus, regular validation epochs, non-transferable identities.
6. Fractal ID
Fractal is more pragmatic and regulatory-friendly. It performs traditional KYC (passport, selfie, etc.), but gives users verifiable credentials (like "verified and over 18") they can reuse across Web3. Instead of sharing your whole ID with every dApp, you just prove attributes.
It’s perfect for compliance-heavy use cases. But it’s also centralized: a company holds the power to verify or deny you. Great for DeFi on-ramps and launchpads. Not so great if you’re aiming for anonymity.
Strengths:
- High-assurance compliance-ready verification.
- Dataless approach reduces privacy risks.
- Integrated with Polygon ID and DID standards.
Limitations:
- Centralized trust model.
- Not censorship-resistant.
- Unsuitable for anonymous or pseudonymous users.
Technical flavor: Verifiable Credentials (VCs), Decentralized Identifiers (DIDs), privacy-enhancing KYC, Polygon ID integration.
7. Polygon ID
Polygon ID brings zero-knowledge proofs into the mix. It lets users prove facts about themselves (like being over 18 or holding a credential) without revealing personal data. Credentials are issued by trusted parties, stored in your wallet, and used to generate ZK-proofs.
It’s arguably the most privacy-preserving system on this list. You control your identity, issuers verify facts, and dApps don’t have to store your info. But it’s early, and adoption still needs to grow.
Strengths:
- Maximum privacy with selective disclosure.
- Fully self-sovereign and interoperable.
- Smart contract verifiable.
Limitations:
- Needs bootstrapping of credential issuers.
- User experience and education are still early.
- Does not natively solve Sybil resistance (requires an external issuer).
Technical flavor: zkSNARKs, selective disclosure, DID registry on Polygon, decentralized on-chain verification.
8. SRGATE
SRGate is a decentralized uniqueness verification layer that will allow users to verify their uniqueness once and use that proof across any app on any chain. Instead of verifying separately for every platform, SRGate will act as a universal pass that confirms a person’s uniqueness without revealing their identity or personal data.
It is designed to solve a core problem in Web3 and even in Web2 - how to ensure that each participant is a real, unique human without relying on centralized verification methods like KYC. It will give users control over their own identity, allowing them to decide where and how they authenticate while keeping their biometric data secure and private.
SRGate is Humanode’s answer to the mess of identity on the internet. It’s a biometric-based, privacy-preserving, reusable proof of personhood system. No KYC, no documents, no password resets. Just a one-time, cryptographically secure biometric scan that proves you’re a real, unique human, without exposing anything about who you are.
And then you reuse that proof across any App both on chain and in traditional Web.
It’s like if someone combined Face ID, zero-knowledge proofs, and a wallet – and made it cross-chain, decentralized, and actually private.
Strengths:
- Sybil resistance without identity or KYC.
- No centralized databases.
- No way for anyone even Humanode to see your biometric data.
Limitations:
- Relies on one Biometric Modality only
- User experience is still early stages
- Still expanding ecosystem support.
Technical flavor: Confidential Virtual Machines (CVMs), cryptobiometrics, biometric-to-wallet mapping, SRGate contracts callable by any EVM chain, APIs.
9. MetaMask & WalletConnect (Web3 Wallet Logins)
MetaMask, WalletConnect, and similar wallet-based login tools are the most common gateways to Web3. While they don’t verify you’re human, they let you prove ownership of a wallet address through cryptographic signing.
Strengths:
- Seamless login experience across dApps.
- Full pseudonymity with consistent identity.
- Easy to use and widely supported.
Limitations:
- No Sybil resistance, one person can create endless wallets.
- Susceptible to private key loss.
- Provides no inherent uniqueness or trust score.
Technical flavor: ECDSA signatures, Ethereum-compatible wallets, WalletConnect protocol, cryptographic wallet authentication.
Each of these platforms tackles identity and Sybil resistance from a different angle: hardware, social graphs, verification ceremonies, aggregated credentials, zero-knowledge proofs, or good ol' KYC. None are perfect. All are evolving. But together, they reveal just how rich and experimental this space has become.
Next, we’ll take these platforms head-to-head. What do they offer? Where do they fail? And which ones might actually be capable of powering a global, one-person-one-account future without compromising privacy, security, or decentralization?
Global Login Solutions – Comparison
| Platform | Login Methods | Privacy Controls | Sybil Resistance | Interoperability | Decentralization |
|---|---|---|---|---|---|
| LogIn with Google | SSO with personal data sharing | Consent-based data sharing, but extensive data tracking | None; based on email or phone number | High (works across most platforms) | Centralized control; risk of data breaches and lockouts |
| LogIn with Apple | SSO with enhanced privacy | Hide My Email; no app tracking | None; Apple ID-based | Medium (mostly within the Apple ecosystem) | Vendor lock-in, limited openness |
| Login with Facebook | SSO linked to social profile | Limited control; track interactions for ads | Very low; over 1B fake accounts removed in Q4 2024 | High, but mainly integrated with Facebook-connected services | Surveillance, manipulation Sybil attacks |
| BrightID | P2P connections, graph-based analysis | Fully user-controlled. No personal info collected. Network only sees anonymized graph connections | Medium. Prevents mass Sybil accounts through social graph analysis. Vulnerable to collusion or gaming via dense clusters | Medium. Integrated with Gitcoin Passport, some DAOs. Needs active adoption | High. Fully open-source, governed by BrightDAO, decentralized verification model |
| Fractal ID | Government ID + selfie | "Dataless KYC" approach. Data deleted post-verification. Verifier sees only status, not full identity | Strong for compliance. Each verified user passes full KYC. However, not designed for anonymous or non-KYC use cases | Medium. Integrated with Polygon ID. SDK available for partners | Low. Centralized company controls the identity process. No DAO or community governance |
| Gitcoin Passport | Social account verification (Twitter, GitHub) | User owns their credentials. No raw personal data shared, only verifiable claims via DIDs | Medium. Aggregates trust from multiple sources. Can’t guarantee uniqueness but makes attacks expensive and time-consuming | High. Works across EVMs, easy integration via APIs and SDK | Medium. Runs under Gitcoin DAO. Attestations rely on centralized + decentralized sources |
| Idena | Global synchronous CAPTCHAs (Flips) | Fully pseudonymous. No personal data or biometrics. Just CAPTCHA-solving behavior | Strong. Time-locked Turing tests make multiple accounts impractical unless you can be in two places at once | Low. Primarily native to Idena chain. Limited Web3 interoperability | High. Consensus and validation fully decentralized. No central authority for identity |
| MetaMask/WalletConnect | ECDSA wallet signature | None. No identity, no uniqueness. Pure wallet access. No privacy protections for linking wallets to activity | None. Anyone can create thousands of wallets. No uniqueness, no real Sybil resistance | Very High. Compatible with nearly all Web3 dApps and chains | Medium. Wallet providers are centralized, but infra is decentralized |
| Polygon ID | Issuer credentials + zkSNARK proofs | Maximum. Users control their data and share zero-knowledge proofs only. Verifiers don’t see the underlying info | Weak by itself. Needs third-party credentials (e.g., BrightID) to ensure uniqueness. Offers private proof, not uniqueness | High. Native to Polygon but can verify across EVM. Open to issuers | Anyone can issue, hold, and verify credentials |
| Proof of Humanity | Video selfie + vouching + Kleros | Public video and vouching. No personal ID needed but identity is publicly linked to wallet | Strong. Vouching, video, challenge period, and Kleros court make mass Sybil entry hard | Medium. Works with Gitcoin, Democracy Earth. Still mostly Gnosis Chain-bound | High. Fully community-run via DAO. Transparent and forkable. Uses decentralized arbitration |
| SRGate (Humanode) | Biometric uniqueness via cryptographically secured face scan | Strong. Cryptobiometrics are processed in encrypted environments (CVMs) and never exposed | Very Strong. One biometric = one wallet. Impossible to create duplicate accounts. Built for one-person-one-account logic | High. Callable from any EVM chain via SDK and APIs. 0auth via APIs for Web2 | Medium-High. Gradually expanding to One person, One vote governance and many biometric providers |
| Worldcoin | Iris scan via Orb | Uses ZK + secure MPC to prevent linking biometric data to user identity. User doesn’t control raw data | Strong. Based on biometric iris scan; high resistance but limited by Orb availability and centralized hardware | Medium. Offers SDK, but ecosystem integration still in progress | Medium. Biometric hashes stored on-chain, open-sourcing in progress, but infra still centralized |
5. The Humanode Vision: SRGate
Let’s be real. Most identity systems today, whether built on blockchains or not, ask you to give up something. Your privacy. Your time. Your face. Your trust. And at the end of it all, you're still left proving you're not a bot every time you join a new platform.
That’s exactly what SRGate is here to change.
What is SRGate?
SRGate is Humanode’s answer to the mess of identity on the internet. It’s a biometric-based, privacy-preserving, reusable proof of personhood system. No KYC, no documents, no password resets. Just a one-time, cryptographically secure biometric scan that proves you’re a real, unique human, without exposing anything about who you are.
And then users reuse that proof across any app (on-chain and off-chain)
It’s like if someone combined Face ID, zero-knowledge proofs, and a burner wallet, and made it open, decentralized and actually private.
Built for Real Decentralization
SRGate isn’t just a clever tool. It’s a shift in the trust model. There are:
- No centralized databases.
- No identity authorities.
- No way for Humanode (or anyone else) to see your biometric data.
That’s because the biometric processing happens inside Confidential Virtual Machines (CVMs) using AMD SEV-SNP. These are isolated, hardware-encrypted environments that can’t be tampered with, not even by cloud admins.
What’s produced from your biometric scan isn’t a face or an iris hash. It’s an opaque cryptobiometric biotoken, a unique proof that maps to your EVM wallet without revealing any personal information.
From Verification to Login Layer
Here’s where it gets spicy: SRGate isn’t just a verification system. It’s aiming to become a new kind of login, one that’s built on the idea of human uniqueness.
Imagine signing into a dApp, forum, airdrop, or DAO, and instead of clicking “Login with Google” or connecting 14 wallets, you just prove you’re a human. One human, one click, one token.
That’s where this is heading. A login layer that:
- Respects your privacy.
- Can’t be gamed by Sybils.
- Works across any chain that wants it.
Where It’s At Today
As of now, SRGate is still in development. But the foundational components are already live in the Humanode ecosystem:
The next steps? Developer tooling, integrations, and plug-and-play login components that Apps can use.
If the current login world is built on surveillance and centralization, SRGate is building for the opposite: a human-first, decentralized internet where proving you're real doesn’t mean giving up your identity.
So
At this point, you're probably wondering: which one actually works?
Truth is, there’s no silver bullet. Each system we’ve looked at, centralized or decentralized, has strengths, tradeoffs, and assumptions baked into its design.
We’ve seen the contenders. Some verify skills. Some verify credentials. Some aim to give users more control over data (like Polygon ID or SRGate). Others focus on building public goods (like BrightID or PoH). A few are compliance-first (Fractal ID), or social-first (Gitcoin Passport). Then you’ve got the crypto-native wallet logins like MetaMask, which are flexible but identity-agnostic, and the biometric heavyweight, Worldcoin, trying to boil the ocean with Orbs. But only a few truly offer proof of personhood, and fewer still aim to become the One Login that works everywhere.
The broader takeaway?
We’re entering a future where Login becomes modular. You might prove your dev skills via GitHub (in Gitcoin Passport), and prove you're over 18 via Polygon ID, all without ever doxxing yourself. The best stack might not be a single platform, but a composable mix.
But when it comes to solutions that aims to become One Login that works everywhere, we have very few.
And that’s what makes this space exciting.
Because maybe, just maybe, we can move past surveillance logins, data leaks, and pay-to-vote governance... toward a digital world where every human gets one account, equal rights, and full privacy.
That’s not just a better login.
That’s a better internet.

