Revolutionizing identity verification: An introduction to Proof of Personhood (PoP) protocols

In this paper, Proof of Personhood (PoP) protocols — types of identity verification mechanisms that aim to protect digital space from identity fraud — are explored. The narration starts with an overview of the PoP history, advantages and challenges, and primary use cases. Then, the main identity verification mechanisms, their benefits and limitations are outlined alongside initiatives utilizing them. Finally, a comparison of PoP protocols is provided. By highlighting the potential of PoP protocols to revolutionize the way we see identity verification in the Web3 era, this paper contributes to the ongoing discourse around digital identity and provides a foundation for future research and development in this area.
Introduction
In recent years, the need for reliable and secure identity verification systems has become increasingly important. Traditional methods of identification have proven to be susceptible to security breaches and fraud. In response, Proof of Personhood (PoP) protocols have emerged as a promising solution for identity verification.
This paper provides an introduction to PoP and its potential as a revolutionary technology for identity verification. PoP refers to an efficient tool capable of creating a truly decentralized protocol to counter malicious attacks on online platforms, mainly attacks with the utilization of multiple fake virtual identities such as the Sybil one. These protocols rely on cryptographic algorithms to ensure the security and integrity of identity verification.
PoP exhibits great potential in transforming the authentication process and guarding against security breaches and fraud, despite the difficulties it may encounter. The paper overviews PoP, and its benefits over traditional identity verification methods, and considers the challenges and risks of PoP including privacy concerns, scalability, and interoperability with existing systems. It also explores the various use cases of PoP, such as identity verification, democratic governance, public goods funding, Universal Basic Income (UBI), anti-Sybil tools and airdrops, et cetera.
We discussed the most notable identity verification mechanisms and PoP initiatives, including Kleros, BrightID, Idena, Humanode, Worldcoin, Governor DAO, Anima, Upala, and Gitcoin Passport. A comparative table of PoP initiatives is provided. By exploring them, and analyzing their potential and limitations, this paper seeks to inspire further research into the potential of PoP.

Part I. Understanding PoP
This part aims to provide a comprehensive understanding of PoP. The section will begin with an overview and history of the concept. The focus will then shift to the unique components of PoP that distinguish it from traditional approaches, such as Proof of Work (PoW) and Proof of Stake (PoS). Finally, this section will explore the various use cases where PoP may be successfully implemented, and delve into the advantages of PoP over other methods of identity verification, as well as its challenges and risks. By the end of this section, the reader will have a solid foundation of knowledge on PoP and its potential for transforming the field of identity verification.
From concepts to definitions: Tracing the evolution of PoP
The goal of creating a distributed system in which each unique human will have only one ID has remained for decades. It has become even more relevant and hot with the proliferation of the internet, the increase of Sybil attacks, and the simplification of their conduct.
Basically, Sybil resistance in the system refers to the ability of a system to resist attacks from malicious actors attempting to create multiple fake identities, or Sybils, in order to gain control or influence over the system. It is named after the subject of the book, a woman diagnosed with dissociative identity disorder named Sybil.
The term “Sybil” was coined by John R. Douceur (2002). He defined Sybil attack as
“an attack wherein a single entity masquerades as multiple entities or nodes within a network to gain a disproportionately high influence within the network or to subvert the network’s operation altogether.”
Answering the challenges of times, to tackle Sybil attacks, several mechanisms have been developed. The basic ones are KYC (which means Know Your Customer and sometimes Know Your Client, which is the process of identifying and verifying the client’s identity), Turing tests like CAPTCHAs (a contrived acronym for Completely Automated Public Turing test to tell Computers and Humans Apart) introduced by von Ahn et al. (2008), social trust and graphs, and other integrated methods.
However, not all of them provide privacy, and anonymity, requiring users to share their personally identifiable information (PII) which may include names, addresses, emails, passport numbers, financial account numbers, and others.
One early privacy-preserving approach was proposed by Bryan Ford, Jacob Strauss, et al. (2008) to create anonymous one-per-person credentials for use in distributed systems. It was basically pseudonym parties, in which participants gather periodically at in-person events and leverage the fact that humans can physically be in only one place at a time:
“A pseudonym party is a gathering where participants create new online identities, also known as pseudonyms, and establish strong links between their offline and online identities. The process involves the verification of each participant’s real-world identity, the creation of a new cryptographic key pair for each pseudonym, and the establishment of a web of trust among the participants. The pseudonyms can then be used for a variety of online transactions, such as electronic voting, online auctions, or anonymous blogging, with the assurance that each participant is only using one pseudonym and that each pseudonym corresponds to a real-world identity.”
Vitalik Buterin (2014) was also one of the first researchers who raised the ‘unique human problem’ and propose the creation of a ‘unique identity system’ for crypto networks:
“… final unique human problem is the need for a system of reputation and identity that does not depend on any central authority. This is necessary to create a trustless network of contracts. A possible direction is to use a web of trust system, where each account is associated with a real identity, which is itself associated with a certain amount of reputation. Alternatively, one can use a centralized identity system, but one that is controlled by the users rather than by any one central organization.”
Anti-Sybil at its very core, such a system would have given each human one and only participation token.
A few years later, the term PoP was suggested in an academic paper by Borge et al. (2017) as they introduced PoPCoin cryptocurrency. According to them,
“Proof-of-personhood is based on the concept of accountable pseudonyms. The idea is to link virtual and physical identities in a real-world gathering (e.g., a party) while preserving users’ anonymity.’’
Also, there are certain nuances and variations of PoP naming. Thus, the PoP mechanism is also usually called Proof of Existence (PoE), or Proof of Human Existence (PoHE). For example, Chopra, Gupta and Lambora (2019), define PoE as a blockchain-based mechanism that “enables users to verify the existence of a digital document without disclosing its contents and without requiring any trusted third party.”
Mainly, PoP can be defined as a type of Sybil-resistant identity verification mechanism that uses unique attributes and characteristics of individuals to verify their identity. By leveraging decentralized networks and cryptographic algorithms, PoP protocols aim to provide a more secure and cost-effective alternative to traditional identification methods.
Currently, there are several crypto initiatives that are implementing PoP in diverse approaches to bolster their network’s security and identity verification, thereby revolutionizing how we think about decentralization and tech, and promoting a more secure and human-centric future.
Exploring the unique components of PoP
PoP protocols have two key components that differentiate them from traditional identity verification mechanisms. These components are:
- Personhood
PoP protocols require users to prove that they are unique human being through various means, such as, for example, biometric data, or community verification. Mainly, PoP protocols rely on a unique human recognition process to identify individuals, as opposed to traditional identity verification methods that rely on documents or credentials. This process allows for a more secure and reliable identification method that is not susceptible to fraud or impersonation.
- Decentralization
PoP protocols utilize decentralized verification systems, where a network of nodes or peers verifies the identity of an individual rather than a centralized authority. This system reduces the risk of data breaches and provides greater control over data for individuals.
PoP: Sybil resistance beyond PoW and PoS
PoP is a novel approach to identity verification that when built on the Layer 1 level distinguishes itself from traditional Sybil deterrence mechanisms, such as Proof of Work (PoW) and Proof of Stake (PoS) that currently dominate in the space.
In a nutshell, PoP is designed to check whether every person in the network is unique and has a singular identity and ensures it. Bringing equality and Sybil resistance to the system, the PoP mechanism in Layer 1 networks guarantees every individual the same amount of weight in the consensus, voting power, and rewards creating a democratic and fair peer-to-peer network.
In contrast, PoW and PoS networks grant voting rights and rewards in proportion to users’ economic investments in an activity or resource, stake, or computational power, leading to oligopolies and mining pools, which is their main flaw. PoW requires miners to perform a computationally intensive task in order to validate transactions and secure the network, while PoS requires validators to prove ownership of a certain amount of cryptocurrency.
L1 PoP provides an identity verification rooted in human existence, rather than merely computational resources. PoP may be particularly important for certain use cases, such as public goods funding, where identity is critical for accountability and transparency. In this way, PoP has the potential to revolutionize not only the way we verify identity but also the way we distribute resources and govern public goods.
Currently, Humanode and Idena PoP are used to replace PoW and PoS, as they are Layer 1 networks, capable of doing so.
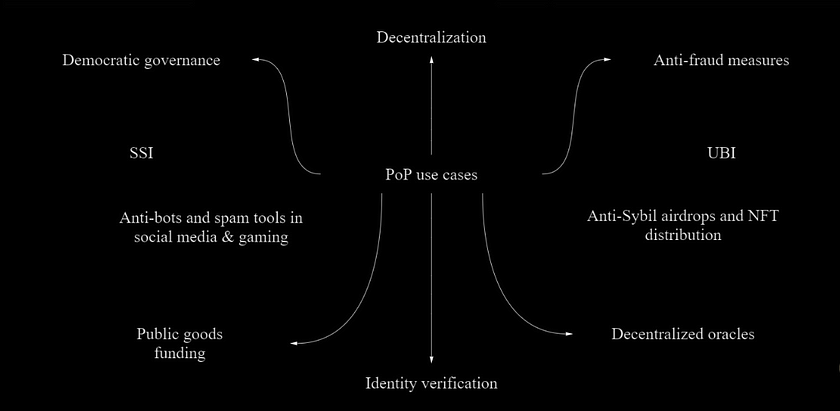
PoP use cases: From SSI to UBI
PoP protocols have several use cases that demonstrate their potential to revolutionize identity verification and establish a more secure and trusted digital ecosystem.
- Identity verification
One of the primary use cases of PoP protocols is identity verification. PoP can be potentially used for identity verification in a decentralized way, ensuring that the identity of the user is verified accurately. This use case is particularly relevant in industries such as banking, healthcare, and voting systems, where secure and efficient identity verification is crucial.
- Self-sovereign identity (SSI)
The notion of SSI was first introduced in a paper by Carl Ellison (1996) that examined how digital identity was created. SSI as a concept emerged later in the early 2010s. PoP protocols can enable SSI, allowing individuals to own and control their digital identities. This can be achieved through PoP mechanisms that enable individuals to generate, manage and control their personally identifiable information (PII) without a centralized third party like a registry, identity provider, or certification authority as well as to share only the information they choose to share.
- Decentralization
The key use for PoP is to eliminate third parties and to ensure that control in the system and voting power are widely distributed. Such a scenario helps proof of personhood networks to avoid the re-centralization that has been observed in proof of work and proof of stake networks.
- Democratic governance
The next use case is democratic governance acceleration and facilitation. Decentralized blockchain architecture should be built in a way that enforces a one person = one vote ethos. The use of PoP protocols in democratic governance can ensure that the voting process is secure and reliable without the need for centralized authorities. By using PoP protocols, it is possible to verify the identity of voters without revealing their personal information, which can help in building a more transparent and democratic system.
The concept that is worth noting here is quadratic voting, an innovative concept that has emerged as a promising solution for community-based decision-making. It was introduced by economist Glen Weyl (2012). Quadratic voting is a voting system that allows voters to allocate their votes non-uniformly, reflecting the intensity of their preferences rather than just their number of votes. As Weyl explains, “The concept of quadratic voting… allows individuals to express how strongly they feel about different issues while discouraging extremists from dominating the debate”.
- Universal basic income (UBI)
The concept of UBI in its early forms has been proposed by various thinkers over time, and its origins can be traced back to the work of philosophers such as Thomas More and Thomas Paine. In modern times, it has been championed by figures such, for instance, as Milton Friedman. The specific proposal for implementing UBI varies depending on the proponent, but it generally involves providing a regular, unconditional payment to all individuals in a given society, with the goal of addressing poverty, inequality, and other social issues. By using PoP protocols, it is possible to verify the identity of eligible recipients and distribute UBI in a transparent and secure manner, which can help in reducing poverty and improving social welfare. For example, it can be achieved by minting a fixed amount of new currency for each human participant in a given period of time.
- Decentralized oracles
Basically, oracles are mechanisms that provide off-chain data for blockchains. Instead of simple tech due diligence (like in Chainlink) and staking, PoP can provide an alternative solution. Thus, witnesses can be randomly selected from a variety of human participants to reach a consensus on arbitrary evidence. By using PoP protocols, it is possible to ensure that the data is authentic and reliable.
- Public goods funding
Blockchain-based PoP systems are able to make a signal represented by votes and financial obligations transparent at the supranational level. Distinguishing unique identities, adopted on a large scale, can contribute to the social infrastructure and address global challenges connected with ecology, pandemics, inequality, et cetera. PoP protocols can be used to enable secure and transparent funding of public goods, such as open-source software, public infrastructure, and public services. By using PoP protocols, it is possible to ensure that the funding is transparent, accountable, and secure, which can help in promoting the common good.
Glen Weyl and computer scientist Eric Posner proposed a concept of quadratic funding in their papers (2013, 2014, 2015) and later expanded it upon in their book “Radical Markets” (2018). Quadratic funding is a funding mechanism that leverages quadratic voting to allocate funds non-uniformly based on the intensity of support for a particular proposal. As Weyl and Posner note, QF “aims to create a more democratic funding process that can be more easily used by a wider range of individuals and organizations”.
- Anti-fraud measures
Another important use case of PoP protocols is anti-fraud measures. Gao et al. (2020) explain that PoP protocols “can help prevent identity fraud by establishing a secure and verifiable link between an individual and their digital identity.” This can be achieved through various PoP mechanisms, such as, for example, biometric authentication, which ensures that the user is physically present and verifies their identity.
- Anti-bots and spam tools in social media and gaming
It is known that bots manipulate gaming and social media, including signaling methods such as likes and numbers of followers. In networks, where users can create multiple accounts and get rewards for each of them, stable Sybil protection can help in building a more authentic and reliable online community as it can fight the spread of fake experiences, misinformation, as well as digital advertising scams.
- Anti-Sybil airdrops and NFT distribution
Airdrops and non-fungible tokens (NFTs) as recent crypto phenomena suffer from the lack of Sybil resistance. In pursuit of easy-to-get tokens, users often create multiple accounts. PoP is a key component in ensuring fair airdrops and NFT distribution.
Unlocking the benefits
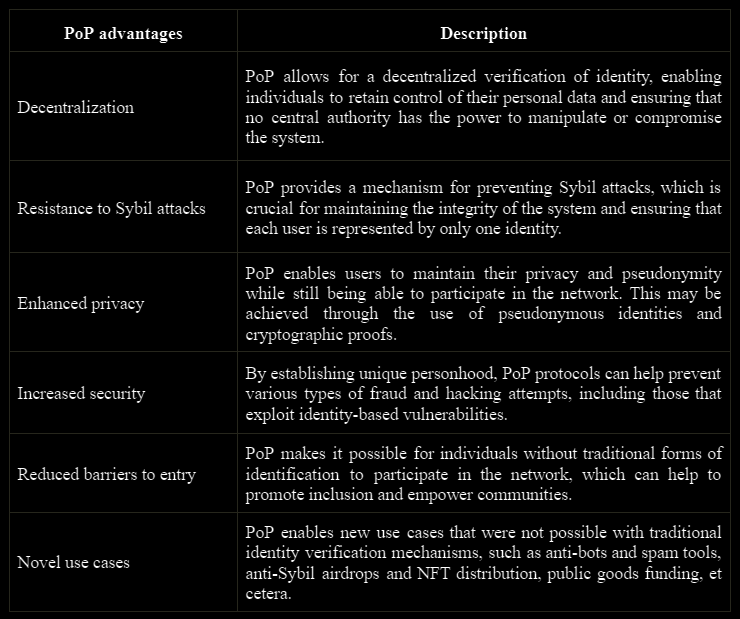
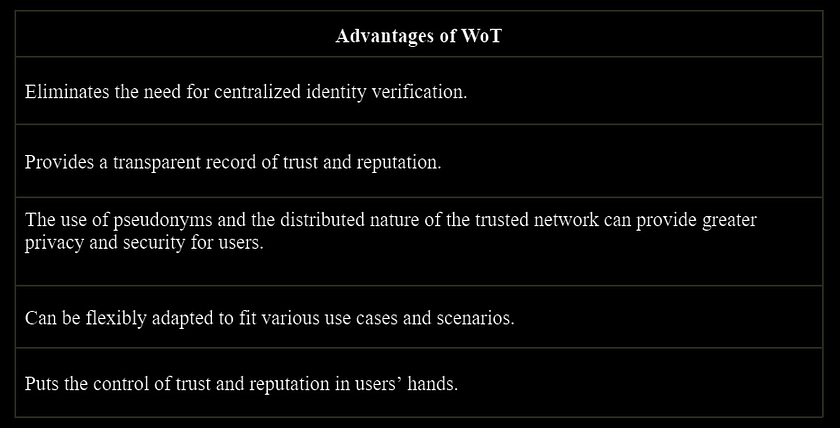
PoP protocols offer several advantages over traditional identity verification methods that are based on sharing sensitive personal information, such as a government-issued ID or a social security number, which can put individuals at risk of identity theft and compromise their privacy.
One key advantage of PoP protocols is increased security. By leveraging advanced cryptographic techniques, PoP protocols make it more difficult for malicious actors to impersonate individuals and engage in identity fraud and improve overall security in the network. On top of that, such cryptographic proofs bring more trust to the data.
In addition, PoP protocols offer an improved user experience. By providing a seamless and user-friendly means of establishing and verifying identity, PoP protocols reduce the need for cumbersome and time-consuming manual verification processes.
Also, most PoP protocols make identity verification more accessible to people without access to traditional forms of identification, such as those living in poverty, refugees, and homeless individuals.
Finally, PoP protocols can be implemented on a large scale, making them suitable for use in a wide range of digital applications and use cases, from financial transactions to online voting and beyond. Such use cases are anti-bots and spam tools, anti-Sybil airdrops and NFT distribution, public goods funding, et cetera.
Basically, PoP protocols offer a promising new paradigm for identity verification in the digital age. By providing a more secure, and user-friendly means of establishing and verifying identity, PoP protocols have significant potential benefits for individuals, businesses, and society as a whole.
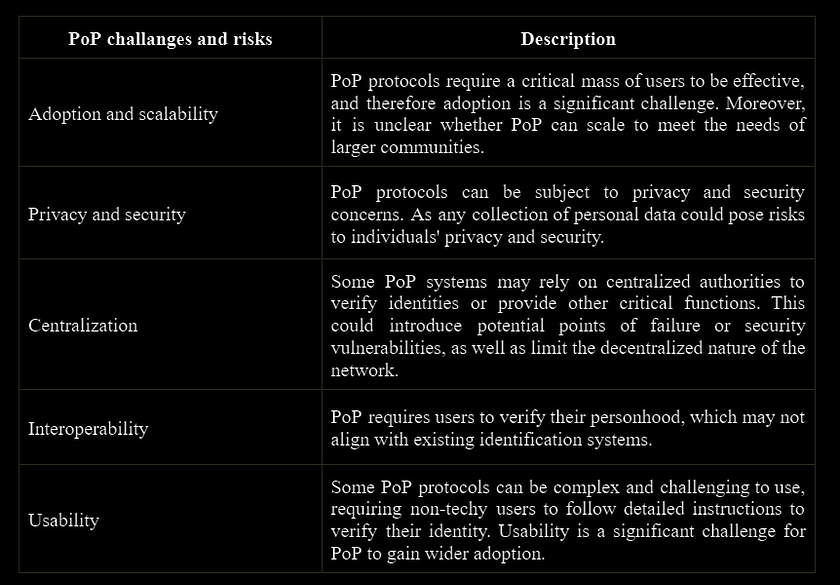
Challenges and risks
Despite the potential benefits of PoP protocols, there are also several limitations and challenges that need to be considered. One significant technical challenge is the difficulty in creating a robust, scalable, and reliable identity verification system. Furthermore, there is a risk of creating a centralized system in the scenario when PoP protocols require a central authority or trusted third party to verify identities. Additionally, there is a risk of identity theft and impersonation if PoP protocols are not designed to protect against these types of attacks.
In summary, PoP protocols hold great promise for revolutionizing the way we verify identity and protect against fraud and security breaches. However, there are significant challenges and limitations that must be addressed to ensure the success of these protocols in the long term.

Part II. Verifying identity: Mechanisms and initiatives in use
As the world becomes increasingly digitized, the need for reliable and secure identity verification mechanisms becomes ever more pressing. A wide range of initiatives have emerged in response to this need, utilizing various techniques to verify the identity of individuals. This part of the paper explores the different identity verification mechanisms and the projects that use them, providing an overview of their strengths and limitations. By examining them, we can gain a better understanding of the current state of identity verification and the challenges that remain to be addressed.
Know Your Customer (KYC)
KYC, or Know Your Customer, is the most common method of identity verification. It is a regulatory requirement in many countries that necessitates financial institutions and other regulated entities to confirm the identity of their customers.
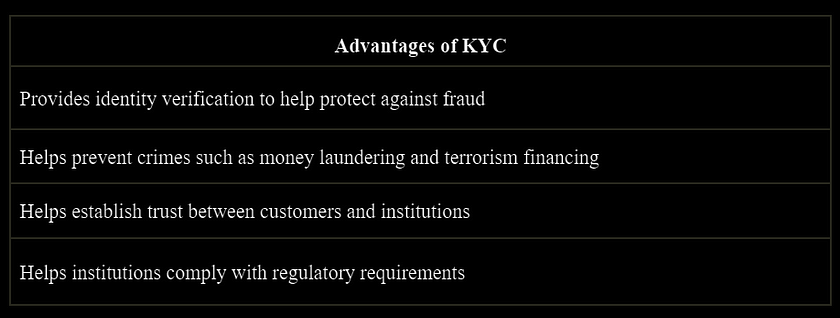
Most decentralized identity solutions require users to do KYC and provide PII, sensitive personal information like government ID, address, photo, etc. This information is then used to verify the customer’s identity using various methods, such as manual verification, electronic databases, and biometric authentication. The problem is that such solutions offer neither security nor privacy, storing users personal information in centralized servers, with direct access to the data given to appointed employees, meaning it can be potentially manipulated, lost, or stolen.
To achieve minimal resistance to Sybil attacks, this approach utilized identity proxies such as phone numbers, credit cards, or IP address verification. It is often easy to obtain numerous identity proxies using techniques such as SMS or IP address spoofing.
Furthermore, KYC processes can be expensive, and time-consuming as the customers must go through a series of steps to complete the verification process. Despite being a time-consuming process, KYC can still be inaccurate in verifying the customer’s identity due to software, human error, or fraudulent documents. Additionally, the collection and storage of personal data during the KYC process can raise privacy concerns for customers.
Another limitation of KYC is exclusion. It can exclude certain segments of the population who may not have the necessary documents to verify their identity, such as refugees or those without a permanent address. This exclusion can be detrimental to these populations and limit their access to financial services and other opportunities.
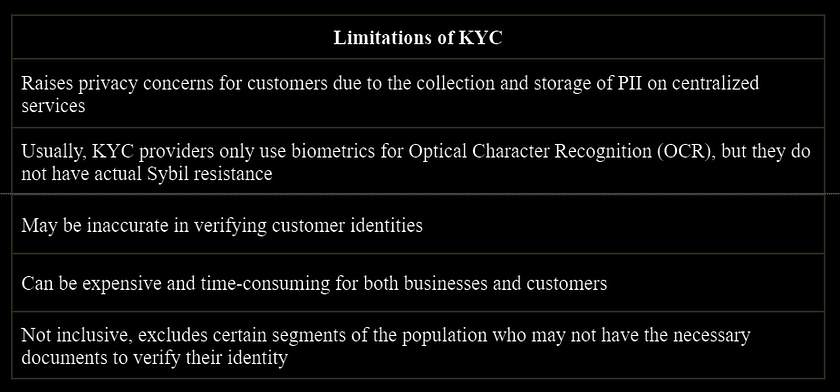
The emergence of new technologies such as blockchain and PoP protocols have the potential to revolutionize KYC by providing more efficient and secure identity verification mechanisms. PoP can protocols provide an authentication mechanism that relies on cryptographic techniques to verify an individual’s identity without revealing sensitive information, making it an attractive option for KYC processes. By leveraging such cryptographic techniques, KYC can be streamlined and made more transparent, and secure, while also reducing the burden on customers.
Thus, in 2020, Synaps’ startup initiated a user-friendly decentralized KYC solution to simplify fundraising and access to investment on the Web3. The project was created with the vision to optimize and streamline the identification path, making connected communities a safer place.
Web of Trust (WoT)
The Web of Trust (WoT) is a trust model that can be used to establish the authenticity and reputation of individuals or entities within a network. The concept was first put forth by Pretty Good Privacy (PGP) creator Phil Zimmermann (1992).
It was originally developed as a method for verifying the authenticity of email senders but has since been applied to other online activities such as website authentication and secure communication.
Web of trust is a decentralized trust model and a cryptography concept used in PGP, GNU Privacy Guard (GnuPG), and other PGP-compatible systems. It is based on the ground of the authenticity establishment of the binding between a public key and its owner.
In this model, each user has a trust rating that is determined by the ratings of other users they are connected to. The more trustworthy the user’s connections, the more trustworthy the user is perceived to be. This creates a decentralized system of trust that does not rely on centralized authorities or institutions.
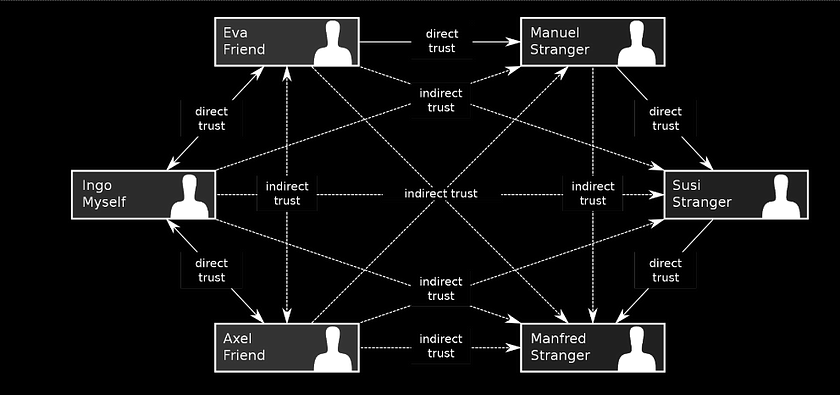
The WoT model’s decentralized nature allows for greater security. As the WoT relies on trust relationships between individuals, there is no central authority or single point of failure that could compromise the security of the system.
However, the WoT model also has some limitations. For example, while promising, it has not yet been widely adopted in practice due to its usability challenges. WoT relies on the reputation and trustworthiness of individuals, but this can be difficult to establish, as individuals may have different criteria for what constitutes a trustworthy individual. The trust model of WoT has certain limitations since trust is subjective and varies between individuals.
Additionally, the WoT model may be vulnerable to attacks by malicious actors who attempt to manipulate trust relationships in order to gain access to sensitive information or resources. On top of that, the effectiveness of WoT is limited to the size and activity of the network, as a larger network provides more opportunities for establishing trust and verifying identities.

Kleros and Proof of Humanity
Proof of Humanity (or PoH) is a social identity verification system for humans on Ethereum.
According to C. Lesaege, F. Ast, and W. George (2019), Kleros is an Ethereum-based decentralized application that works as a decentralized third party to arbitrate disputes in every kind of contract, from very simple to highly complex ones. Every step of the arbitration process (securing evidence, selecting jurors, etc.) is fully automated. Kleros relies on game theoretic incentives to have jurors rule cases correctly. The result is a dispute resolution system that renders ultimate judgments in a fast, inexpensive, reliable, and decentralized way.
The Kleros team proposed the Proof of Humanity PoP protocol, a solution for identity combining WoT, with reverse Turing tests, and dispute resolution to create a Sybil-proof list of humans.
The Proof of Humanity reputation-based WoT relies on users’ information about themselves utilized for verification. Humans who wish to be included in the registry submit photos, bios, and video recordings. This PII is stored using the IPFS (InterPlanetary File System). Registered profiles collect Democracy Earth’s UBI Tokens.
Users who are already in the Proof of Humanity registry vouch for others registering with a certain amount of financial stake. By vouching, they guarantee that the users they vouch for exist and are not duplicates of another entry in the registry. To incentivize the maintenance of the registry, vouching deposits serve as a bounty, available for anyone able to correctly identify false positives in the registry.
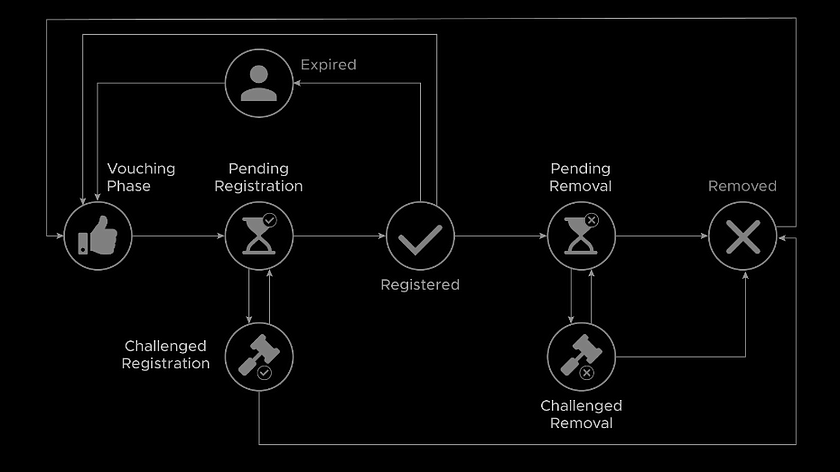
Despite the protocol’s innovation and the numerous advantages, it compromises the information of members by requiring video proof and other additional information, which may demotivate regular users. Furthermore, the protocol requires a deposit in ETH to generate the Proof of Humanity profile.
BrightID
BrightID is a social identity network that allows people to prove to applications that they aren’t using multiple accounts.
BrightID is an identity system for the decentralized web. It solves the unique identity problem through the creation and analysis of a social graph. Its graph relationships are designed to identify true and Sybil identities based on the node’s position with respect to trusted seeds.
BrightID uses a cross-network trust protocol built by graphically displaying social ties with the optional input of trusted seed IDs. The purpose of this protocol is to allow users to provide proofs that they are not using multiple accounts in the same application.
BrightID is the solution most characteristic of the Intersectional Identity paradigm, formalizing the social connection to allow different nodes to join the system and set and customize their own evaluation criteria. With this value, there are no obvious restrictions on trusted seeds in the BrightID social graph. Any application using its authentication solution can create its own BrightID node with trusted seeds available. BrightID is designed to interact with major Web2 social media platforms.
The social graph serves as a common base for all nodes, but the analysis of the same graph can be different, so the protocol does not require consensus between nodes. Applications can either run their nodes centrally or privately, sharing their analysis and validation results only with themselves, or they can provide a higher level of decentralization, allowing any user to run validation and select results from a large number of nodes.
To control Sybil attacks, BrightID runs GroupSybilRank, a modification of the SybilRank algorithm, to evaluate the anti-Sybil score of network participants based on the similarity between groups.
However, BrightID has several challenges to overcome in terms of Sybil resistance, decentralization, and sovereignty. The project is limited to a small source network, so there are no established ways for individuals or groups who are completely independent of the existing network to authenticate themselves. Nonetheless, new hosts could potentially define new validation methods that would allow user groups to be validated. Scaling is an issue. One possible solution is to partner with existing social media platforms that cover a wide network of users, bringing scalability while maintaining decentralization.
Another limitation, common to many networks, is that decentralized, pseudonymous ID users could rent their verification to someone else.
And last but not least, the verifications generated by BrightID may be considered too permissive or too strict. On one hand, “connection parties” allow someone to create a small number of Sybils by being a tourist among different verifying groups. On the other hand, “yekta” verifications require proximity to the center of the graph, which isn’t practical for most new users.
Reverse Turing tests
Turing tests are a type of challenge-response test used to determine whether or not a machine can exhibit human-like intelligence. The Turing test originally called the imitation game was introduced by British mathematician and computer scientist Alan Turing (1950) in his paper ‘Computing Machinery and Intelligence’ while working at the University of Manchester. According to Turing, “The question, ‘Can machines think?’ is equivalent to the question, ‘Can machines do what we (as thinking entities) can do?’” (Turing, 1950). Turing tests typically involve a human evaluator who engages in a conversation with a machine and tries to determine whether the responses are being generated by a human or a machine. As noted by Harnad (2000), “A machine passes the Turing Test if a human judge, after posing some questions to both the machine and a human being, cannot reliably distinguish which is which.” While Turing tests have been criticized for various reasons, they remain a popular tool for evaluating the intelligence of machines.
Reverse Turing tests are Turing tests in which the objective or roles between computers and humans have been reversed. They have been used in a variety of contexts, including as a means of authentication for online systems. In this context, reverse Turing tests are often used to verify that a user attempting to access a system is indeed human and not a machine or bot. This type of test is commonly known as a CAPTCHA (Completely Automated Public Turing Test to Tell Computers and Humans Apart). The use of CAPTCHAs as a means of preventing automated access to online systems has become widespread in recent years, due to the increasing prevalence of bots and other automated tools that can be used for malicious purposes such as spamming or denial-of-service attacks.

Despite their widespread use, reverse Turing tests and CAPTCHAs have been subject to various criticisms and limitations. Some researchers have questioned the ability of reverse Turing tests to verify the user’s real-world identity or prevent identity fraud, while others have noted the increasing sophistication of bots and automated tools that can bypass CAPTCHAs. Additionally, CAPTCHAs have been criticized for being difficult for some users to complete, particularly those with visual or cognitive impairments.

Idena
Idena is the PoP blockchain where every node is linked to a crypto identity — one single person with equal voting power.
Idena is one of the first PoP blockchains, an open-source project created by an anonymous group of engineers in October 2018. It is driven by eco-friendly Proof-of-Person consensus where each node is associated with a crypto identity representing a single individual with equal voting power.
The Idena Network achieves Sybil-resistance by combining human-generated reverse Turing tests, also known as FLIP tests — CAPTCHAs, with elements of a virtual pseudonym party.
Every unique human can become an Idena validator. To start mining, they only need to prove you are a unique human, without disclosure of any personal data.
Idena users must attend live authentication ceremonies held simultaneously for the entire network frequency is determined by the size of the network. During these synchronous events, they must complete the FLIP test suite within a limited amount of time. After that, users must create new tests.
The time limit prevents a single person from solving more than one set of FLIPs, while the human-generation aspect provides machine-learning resistance. In addition, the protocol protects privacy because it does not include any data other than evidence of conscious cognitive ability.
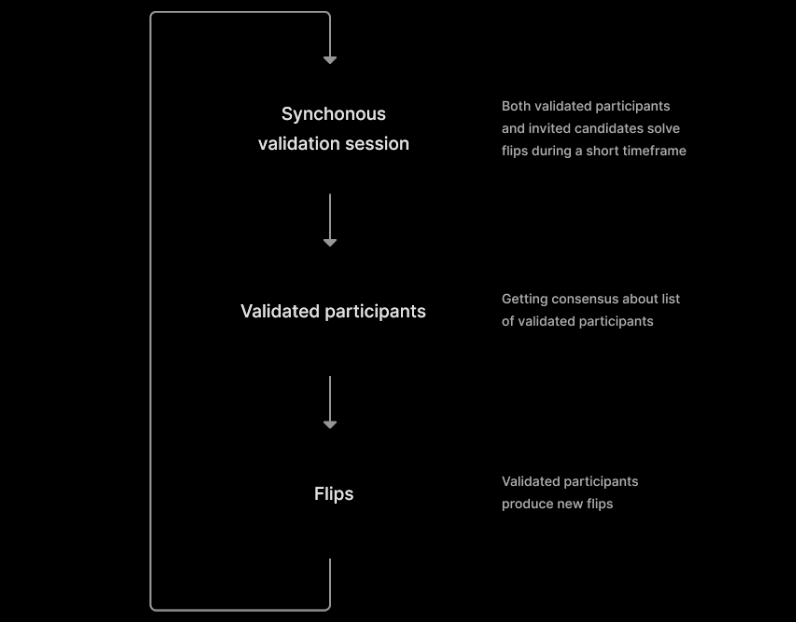
Given that tests cannot be solved by existing AI, Idena successfully provides proof of personhood. It remains to be seen whether the project’s Sibyl resistance strategy can withstand the dynamic development of AI associated with neural networks and deep learning.
Moreover, Idena requires new members to submit an invitation code in order to be able to join their first authentication ceremony, increasing security. The code can only be obtained through existing members, thus creating a web of trust. This also extends to the reward system as at every ceremony, the network rewards all of its members with its IDNA tokens.
The most notable flaw of the Idena design is the significantly higher coordination overhead to achieve a repetitive concurrent FLIPS solution. All Idena nodes must constantly participate in synchronous events, otherwise, their identities will expire.
Biometrics
Biometrics as a technology for identifying a person based on the measurement and statistical analysis of its unique physical or behavioral characteristics is a phenomenon of high importance in modern society. It is a key to anchoring digital identity and the most suitable means of authenticating individuals in a reliable and fast way.
Overall face shape, fingerprints, palm print, hand geometry, iris recognition, DNA, dental records, and even more subtle metrics like heartbeats or odor — modern technology can measure extremely complex inputs to find identity matches or verify identity. And experts argue that growth trends in mobile identity verification and remote onboarding will be sustained due to the recent pandemic spread which leads to the e-passport and health-passport markets explosion.
The benefits of biometrics for identity verification include the high degree of accuracy it provides. In recent years it has become a reliable advanced tool for Sybil resistance. Currently, the highest accuracy in the industry in terms of the possibility of a match between two different people is 1 in 125 million (FaceTec), and the numbers continue to improve (ten years ago, in 2013 there were only 1 in 24 billion).
Biometric modalities, such as fingerprints or facial features, are unique to each individual and cannot be replicated or stolen like a password or PIN. Additionally, biometric verification can be done quickly and efficiently, reducing the time and effort required for identity verification. Biometrics can also enhance security measures, particularly in high-risk environments, by providing an extra layer of authentication.

Biometric technology has been adopted as a reliable method for identity verification due to its unique ability to authenticate an individual based on their inherent physical traits. However, this technology has some limitations that need to be addressed.
One of the main limitations of biometric technology is the risk of data breaches. As biometric data is stored in digital form, it is vulnerable to cyber-attacks and data breaches, which can result in the exposure of personal data to unauthorized parties. Once biometric data is compromised, it cannot be replaced, and individuals may be at risk of identity theft and fraud.
Another limitation of biometric technology is its susceptibility to errors. Factors such as poor image quality, environmental conditions, and physical changes to an individual’s appearance can lead to false rejections or false acceptances. False rejections occur when the system fails to recognize a valid user, while false acceptances occur when the system mistakenly identifies an unauthorized user as legitimate. Still, these limitations are easily addressed by the systems with implemented modern liveness detection mechanisms.
Furthermore, biometric technology may not be suitable for certain groups of people, such as those with physical disabilities or medical conditions that affect their physical features. In such cases, alternative identification methods must be employed to ensure inclusive identity verification.
Also, the use of biometric technology raises concerns regarding privacy and data protection. The collection and storage of biometric data can be perceived as intrusive, and individuals may feel uncomfortable with the idea of their physical traits being stored and shared. It is important to ensure that biometric data is collected and stored in a secure and ethical manner to protect individuals’ privacy and maintain their trust in the system.

* There are False acceptance rate (FAR) that occurs when a biometric system incorrectly identifies an unauthorized person as an authorized one, and False rejection rate (FRR) that occurs when a biometric system incorrectly rejects an authorized person as an unauthorized one.
**Imposter attack is a type of attack where an imposter presents a fake biometric sample (e.g., a photo, a voice recording, or a fingerprint) to the system in order to gain unauthorized access. A spoof attack is a type of attack where an attacker uses a fake biometric sample that mimics the characteristics of a real sample (e.g., a 3D-printed fingerprint or a silicone mask) to trick the system.
Overall, while biometric technology offers several advantages for identity verification, its limitations and risks must be taken into account to ensure its safe and responsible use.
Humanode
Humanode is the crypto-biometric L1 blockchain where 1 human = 1 node that brings Sybil resistance, proper per-human distribution of power and innovative governance models to Web3 using cryptobiometric technology.
The Humanode network bases its infrastructure on human biometrics. Instead of PoW and PoS, Humanode utilizes the combination of proof of uniqueness and proof of existence. Combined with blockchain, it creates the first-ever human-based digital verification layer.
The validators who run the Humanode blockchain are created through private crypto-biometric authentication which is a combination of cryptographic and hardware privacy with matching and liveness detection mechanisms to verify the uniqueness and existence of real human beings. One unique human who is alive can create only one node, and each node has one vote in the system. All the system cares about is if a user is a unique human being and if a user is alive. Humanode utilizes advanced liveness detection technology, due to which the possibility of spoofing an identity without a real human in front of the camera is 1 of 80K (biometrics accuracy is one of the fastest growing areas as it was 1 of 12.5K only ten years ago, in 2012). To achieve the highest accuracy in the biometric industry, 1 in 125M false acceptance rate — FAR, while providing privacy, the project currently implements FaceTec’s biometrics and liveness as well as AMD SEV SNP secure enclaves with the attestation from the chain.
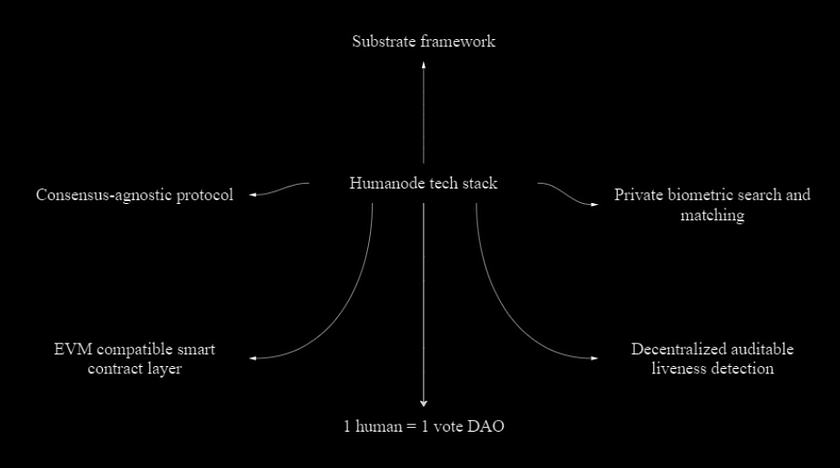
Humanode combines different technological stacks to achieve a decentralized, secure, scalable, and sustainable financial network:
- A bio-authorization module based on neural networks for the private classification of 3D templates of users’ faces;
- Over 60 liveness detection modules for mechanisms for the identification of real human beings;
- Confidential computing and cryptography schemes to achieve privacy of biometric data and computations;
- A Substrate module as a blockchain layer;
- A cost-based fee system;
- A Vortex decentralized autonomous organization (DAO) governing system;
- A monetary policy and algorithm, Fath, where monetary supply reacts to real value growth and emission is proportional.
- Can be installed without writing any code in Discord servers.
In general, the Humanode’s process of identifying a person using biometric templates is divided into two stages:
- The user scans his face for 10–15 seconds with any device over a 3mpx camera. The neural network transforms the video feed into an anonymized 3D template while other modules check if the person in front of the camera is a real one.
- The biometric template and liveness data are encrypted and sent to the biometric confidential servers.
- Confidential biometric servers immediately delete the liveness data and compare a new anonymized 3D template against those already registered in the system. They send the reply in the form of a unique ID to the Humanode chain or directly to an application.
Every User Authentication requires two pieces of data: anonymized 3D template (for matching) and liveness data (to prove the face data was collected from a live person). Liveness data must be timestamped, valid for a certain time, and then removed. Only an anonymized 3D template is saved in the confidential VM for a period of no longer than one year. For each authentication attempt, new liveness data must be acquired. Face data should be encrypted and stored separately from the associated Liveness data to avoid creating a honeypot risk.
The main drawback here is Humanode’s limited chain scalability, up to 10,000 unique human validators, and yet hardware-dependent privacy, which is still better than how biometric data is handled by centralized entities.
Worldcoin
Worldcoin is an open-source identity and financial network on a mission for a global distribution ecosystem for a universal basic income (UBI).
Worldcoin is developing tools that work together to help it achieve its mission. These include:
- World ID — a digital identity designed to help solve many important, identity-based challenges including proving an individual’s unique personhood.
- Worldcoin Token — the token to be globally and freely distributed to people, for both utility and future governance, just for being a unique individual.
- World App — a fully self-custodial app that enables payment, purchases and transfers globally using the Worldcoin token, digital assets, stablecoins and traditional currencies.
Basically, the Worldcoin blockchain introduces a new PoP system that consists of a database of users’ scanned irises that are used to validate their identities and prevent the network from Sybil attacks and users from creating multiple accounts.
From a technical point of view, Worldcoin will use a Layer 2 network and run on top of the Ethereum blockchain. This enables compatibility with many existing tools and services.
To assure widespread adoption, Worldcoin aims to register 2 billion ‘unique humans’ (as of April they have 1.5 billion). Worldcoin claims that getting as many people as possible to use the same currency is the first step. To achieve such big numbers the project rewards every single user with Worldcoin tokens, incentivizing more to join in. Currently in beta, Worldcoin expects to launch in the first half of 2023.
A user’s journey of enrolling for a verified World ID is as follows:
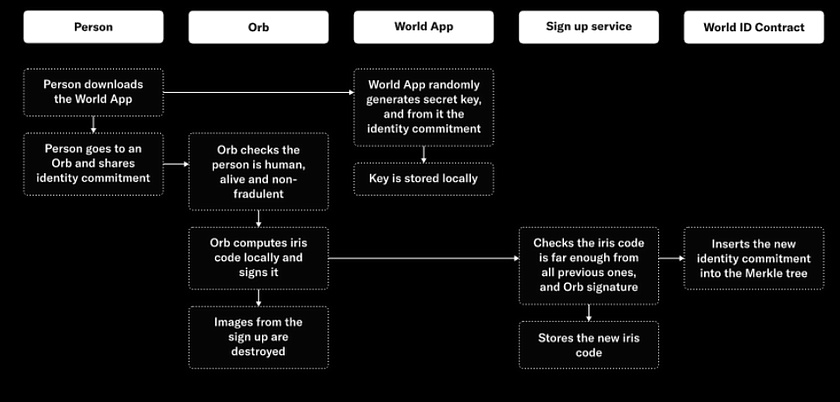
Users who wish to register into the Worldcoin system and claim their free tokens have to first contact an Orb scanning device, a spherical custom-made device that scans people’s eyes. This Orb takes a high-res picture of people’s eyes and distills their iris biometric information into what Worldcoin calls an IrisCode, a set of numbers generated by the Orb that is not linked to users’ wallets or any of users’ personal information. Worldcoin then stores this code in a database and uses it to ensure human uniqueness. Meanwhile, the system erases all other data, including the original image of users’ irises. The only data that remains is users’ IrisCode and all it does is stops users from being able to sign up again.
Worldcoin says it uses people’s iris’ biometric info for its PoP to prove uniqueness in the least intrusive way. It aims to secure the currency without the need for users to surrender too much of their personal info.
The start-up has raised concerns among an increasingly privacy-conscious crypto community. Security and privacy advocates have criticized Worldcoin’s protocol for having their users’ biometric information classified and stored.
However, most of the Worldcoin protocol’s critical systems are designed in such a way that privacy cannot be compromised, even by Worldcoin and its contributors. This is achievable using cryptographically provable mechanisms such as Zero-Knowledge Proofs (ZKPs). Worldcoin uses ZKPs to make it mathematically impossible to link the usage of World ID across applications. Privacy protections such as these go beyond regulatory requirements.
Additionally, privacy and data ownership go hand in hand. Within the Worldcoin ecosystem, the user is always in control of any personal data that is actually captured. For instance, a user can very easily request the deletion of all their personal data with just a few taps in the World App.
Anyone can use the World App and their World ID fully pseudonymously. Users don’t have to provide personal information to register. No emails, no phone numbers, no social profiles, no names, everything is optional.
And ZKPs are used to preserve the user’s privacy and avoid cross-application tracking. Whenever a user makes use of their World ID, ZKPs are used to prove they are a unique human. This means that no third party will ever know a user’s World ID or wallet public key, and in particular, cannot track users across applications. It also guarantees that using World ID is not tied to any biometrical data or iris codes.
Governor DAO
Governor DAO is a decentralized autonomous organization that enables other projects and networks to adopt decentralized governance principles in their own token models and communities.
Governor DAO is a decentralized autonomous organization positioned as the ‘DAO of DAOs’. Governors offer a suite of products and services for projects looking to build DAO qualities in their communities. Such offerings include a Sybil-resistance product for one-voice-one-vote governance and governance bootstraps for new communities, consultations, and smart contract porting.
Governor Decentralized Autonomous Organization (GDAO) allows founders and core team members to hold fewer legal liabilities and offer more open-based ‘Sandbox-like’ services in DeFi, decentralizing project ownership. Driven by its biometrically verified proof-of-existence token, GDAO aims to be a role model for other DAOs. Utilizing biometrics, Governor DAO PoP identity verification is achieved by biometric voice/facial recognition. All biometric information is encrypted as it is produced and is never stored.
In particular, in partnership with biometrics firm Finnovant, Governor DAO has created a portal for biometric authentication of Ethereum wallets. Users enter the portal with a Web3-connected wallet and input face + voice readings. Locally, the user device runs the input information through hundreds of algorithmic indicators to create an encrypted output hash representing the individual.
The Governor DAO biometric verification is based on Finnovant’s Say-Tec facial and voice biometrics, enhancing security in a user-friendly way.
By offering Governance-as-a-Service (GaaS), GDAO anticipates offering proficient security through Proof-of-Existence (PoE) verification and admittance into communal governance discussions, advancements, integrations, and interests.
GaaS intends to resolve these common glitches found in most startup DAOs:
- Insufficient pre-launch stipulations leading to failed governance
- Uninterested token holders seem indifferent to contributing to DAO actions
- Poor governance framework failing to correspond with token circulation
- Short-term opportunists, or ‘Whales’, generate early skewed staking positions
The PoE smart contract uses biometric verification as part of the process to mint a token specific to the GDAO end-user. Completing this process authenticates and verifies individuals (Governors) who wish to use GaaS and prove their existence on other integrated websites. The PoE model is Sybil resistant — meaning that only one wallet per person may be signed up — allowing for fair modeling. PoE offers a decisive progression in building structural DAOs with integrity and is available as a service to third parties who wish to secure their platform for a variety of reasons or create a safer, more fair environment.
Beyond acting as a ‘Digital Identification Card’ PoE also plays a crucial role in transitioning the DAO into a completely decentralized state. Functioning along a bonding curve, PoE is designed to act as a major benefactor of yield returns for GDAO investors. The Governance Vault earnings determine the future progress and success of GDAO and moreover, other DAOs looking to become legitimized blockchain businesses.
The bonding curve assures that subsequent PoE enrollments go up in price over time, so as the viability increases users pay more for a service that is truly unique and is a one-time enrollment fee — this also ensures as we grow out, more funding comes into the Vault via the Payment Splitter.
The project is also subject to privacy concerns since the biometric data is not enough secured.
Anima
Anima helps verify users’ identities and humanity while protecting their privacy.
Anima decentralized identity (dID) protocol allows users to decentralize their identity and share Verified Credentials (VCs) as they see fit. Anima’s solution is multichain, it is compatible with every EVM chain and the team almost finished the integration with Cosmos. Recently, the Anima protocol went live on BNB and bridged all identity use cases — from confirming personhood members to meeting regulatory requirements.
The Anima PoP helps ensure that the community members are unique and human, which helps prevent Sybil attacks and maintains community integrity. By leveraging Anima, anyone can develop a more secure and user-friendly authentication system on their dApps that prioritize user trust.
Anima protocol uses VCs issued by Synaps to link users’ decentralized IDs to their crypto wallets, employing blockchain encryption and wallet signatures for optimal security. The protocol securely stores the VCs, while identity attributes such as names, nationality, and biometric data are kept in a decentralized data storage system called Storj.
These attributes can be used to verify anonymous claims or grouped into proofs for specific use cases. The team has created two proofs, each possessing distinct attributes and usage:
- The Proof of Identity (PoI)
- Concept: This proof is based on users’ official ID documents and biometric data.
- Integrated attributes: Age, nationality, Face scan, name, etc.
- Usage: Check users’ PoI to comply with KYC requirements.
- The Proof of Personhood (PoP):
- Concept: This Proof is based on users’ FaceGraph (using FaceTec biometric technology), a mathematical representation of their face created from a face scan.
- Integrated attribute: FaceGraph
- Usage: The PoP enables the verification of users’ uniqueness and humanity while ensuring that privacy is protected. It can be used for DAO governance, fair reward management, etc.
In April, Anima introduced a new encryption method that allows for public/private keys to be generated directly from the wallet signature, simplifying the data encryption process. By leveraging the wallet signature, Anima can now be integrated into any wallet. The Anima team is currently working on integrating the encryption system change into the dApp, which will enable users to fully leverage your Anima dID. They can now access their Anima with MetaMask, Ledger, Coinbase, Coin98, MultiversX.
Other intersectional approaches
PoP protocols are innovative approaches to identity verification that use unique attributes and characteristics that individuals possess to verify their identity. While PoP has gained traction in the financial and crypto space, there are also other intersectional approaches being developed outside of the frame. By combining various forms of identification and verification, these approaches have the potential to create more secure, efficient, and user-friendly systems.
Upala
Upala is a decentralized digital identity solution that also functions as an anti-Sybil framework for dApps, quality control and unification layer for other identity systems.
According to Upala’s The Pale Blue Paper, Upala is an anti-Sybil system for dApps and decentralized digital identity.
In a nutshell, the Upala project offers a unique approach to digital identity verification through its use of a digital identity uniqueness score, measured in dollars (Price of forgery in Upala terms). The price of forgery is generated through market dynamics enforced by the protocol.
Upala is composed of groups that can consist of anyone, including friends, work communities, DAO members, or even entire identity systems. A user can apply to become a member of different groups.
The system utilizes the concept: ‘Invite only trusted members, or lose your money’. Groups assign a score for each member, denominated in the currency (a stablecoin). Members are given the right to steal from the shared pool of the group they belong to the amount of their score. The act of stealing (a ‘bot explosion’ in Upala terms) automatically deletes their identity.
As a consequence, If the cost of exploiting a group’s approval mechanisms is lower than the provided score, the group becomes a honeypot for malicious users. Which will invade the group, liquidate their IDs and drain the group’s pool. At the same time, groups are incentivized to attract more users by offering higher scores.
This way groups are encouraged to use (or develop their own) approval mechanisms that result in members being more trusted. And even more importantly groups are incentivized to keep their scores accurate — equal to the price of forgery of the chosen approval mechanisms.
This structure creates an identity authentication market. On the supply side, groups try to gather as many users as possible (through subgroups or directly), with the highest reputation (the least risk of explosion). On the demand side, users try to get the highest scores for the least investment of reputation or money.
The funding source of a group pool can be different depending on the purpose of the group. For example, the group may require users to make deposits or the group may be funded by dApp wishing to quality control the user verification method they use.
Upala employs an intersectional lens by enabling different schemes to be created and combined within its protocol. Multiple use cases are possible.
An Upala group can be used to quality control existing identity systems by measuring the price of forgery for each of them or a combination of them.
Groups can also be used to build trust with a group of people, implementing the concept of social responsibility. Any existing DAO can fit into Upala protocol, given that participants are willing to trust each other by providing funds in exchange for distributing reputation.
Groups can also be composed of direct end users or other groups, thus pooling uniqueness scores into larger pools. Moreover, Upala is a protocol that enables the development of different identity systems, all united under the same scoring standard. The protocol can also integrate with existing systems such as BrightID and Idena, allowing for greater interoperability across various digital identity initiatives.
As for limitations, the major vulnerability coded into this model is user avalanche: if an event results in a loss of trust in Upala, an avalanche of people can panic-detonate their identity to confiscate assets, ignoring the reputational consequences. However, it is possible that this scenario is less likely to materialize as trust builds within the system, as well as increased use by third parties for user evaluation.
Gitcoin Passport
Gitcoin Passport acts as an aggregator of decentralized society credentials, proving your trustworthiness without needing to collect personally identifiable information. This process transmits more Sybil resistance out to the entire ecosystem.
Many systems, like Gitcoin Grants, assume each participant is a unique human, and offer rewards for these participants. This makes them vulnerable to Sybil attacks, where a bad actor creates a large number of pseudonymous identities to subvert the service’s reputation system, gain a disproportionate amount of influence, and direct rewards toward extractors.
Credible identity verification and reputation mechanisms are essential to combat this. Applications like BrightID, ENS, and POAP each help suggest whether an account is associated with a real human, but they are only truly powerful when they compose with each other. Projects need a way to evaluate these disparate “identity providers” altogether. That’s where Gitcoin Passport comes in.
Gitcoin Passport is a self-sovereign data collection protocol built with the Ceramic Network, created in line with the Decentralized Identifier (DID) and VC specifications. This data is intended for broad interoperability for any system that wishes to issue or consume VCs to establish the ‘unique humanity’ of an individual through their direct ownership of multiple accounts (Twitter, BrightID), or Web3 assets (ENS). The Gitcoin Passport team continually expands what stamps Passport holders can collect. Stamps represent a web3 citizen’s participation in various groups and communities.
Gitcoin Passport is on its way to becoming the go-to solution for projects to protect their communities, and the identity aggregator for internet citizens to access trustworthy experiences in Web3.

Assessing the landscape: A comparative overview of PoP initiatives
Assessing the current landscape of PoP initiatives is crucial in understanding the various approaches and solutions being developed to address identity verification in the digital age. In this section, we provide a comparative table of several prominent PoP initiatives, highlighting their key features and limitations. By examining these projects side by side, we aim to identify the most promising strategies for implementing PoP and assess the potential impact they could have on the field.
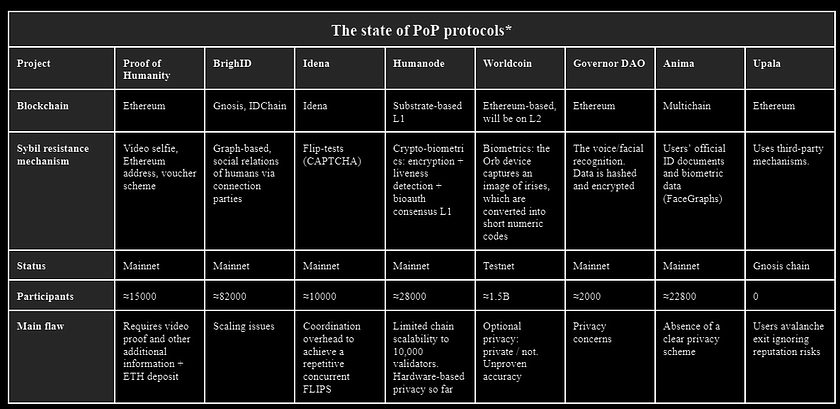
* All data is presented as of the beginning of April 2023.

Conclusion
The current crypto paradigm is dominated by power- and capital-based schemes. Appearing as an alternative, Sybil-resistant human-based PoP protocols allow reorienting of the systems away from such technocratic and oligopolistic narratives, providing true decentralization and democracy.
PoP protocols offer a promising solution to the challenges associated with identity verification in today’s digital world. By leveraging advanced cryptographic techniques, these protocols provide a robust mechanism for establishing and verifying the unique identity of an individual. PoP protocols have the potential to revolutionize the way we think about identity verification, offering a new paradigm for establishing trust and security in digital transactions.
As we have discussed in this paper, the development of PoP protocols is still in its early stages, and many challenges need to be addressed to ensure their widespread adoption. However, the potential benefits of these protocols are significant, including increased security, and improved user experience. PoP projects formalize a new framework for a prosperous and regenerative world, each in its own unique way. They accelerate a new possible human future, where inevitable uniqueness and equality are the main powers.
Moving forward, it will be critical for researchers, developers, and policymakers to work together to continue refining PoP protocols and integrating them into existing digital infrastructure. With continued innovation and collaboration, PoP protocols have the potential to transform the way we establish and verify identity, creating a more secure and trustworthy digital world for all.

References
- Atzei, Nicola & Bartoletti, Massimo & Cimoli, Tiziana. (2017). A Survey of Attacks on Ethereum Smart Contracts (SoK). 164–186. 10.1007/978–3–662–54455–6_8.
- Borge, Maria & Kokoris-Kogias, Eleftherios & Jovanovic, Philipp & Gasser, Linus & Gailly, Nicolas & Ford, Bryan. (2017). Proof-of-Personhood: Redemocratizing Permissionless Cryptocurrencies. 23–26.
- Buterin, V. (2014) “A Next-Generation Smart Contract and Decentralized Application Platform.” https://ethereum.org/669c9e2e2027310b6b3cdce6e1c52962/Ethereum_Whitepaper_-_Buterin_2014.pdf
- Chopra K., K. Gupta and A. Lambora, “Proof of Existence Using Blockchain,” 2019 International Conference on Machine Learning, Big Data, Cloud and Parallel Computing (COMITCon), 2019, pp. 429–431, doi: 10.1109/COMITCon.2019.8862441
- Douceur, J. R. “The Sybil Attack.” https://www.microsoft.com/en-us/research/wpcontent/uploads/2002/01/IPTPS2002.pdf, 2002.
- Ford, Bryan. (2020). Identity and Personhood in Digital Democracy: Evaluating Inclusion, Equality, Security, and Privacy in Pseudonym Parties and Other Proofs of Personhood.
- Ford B. and J. Strauss, “An offline foundation for online accountable pseudonyms”, Proceedings of the 1st Workshop on Social Network Systems, pp. 31–36, 2008.
- Grech A. et al. (2022) Blockchain, Self-Sovereign Identity and Digital Credentials: Promise Versus Praxis in Education. Volume 4–2021 | https://doi.org/10.3389/fbloc.2021.616779
- Ghaffari F. (2022) Identity and access management using distributed ledger technology: A survey. https://hal.science/hal-03315497/document
- Harnad, S. (2000). Minds, machines and Turing: The indistinguishability of indistinguishables. Journal of Logic, Language, and Information, 9(4), 425–445.
- Kavazi D., V.Smirnov, S. Shilina, MD Li, R. Contreras, H. Gajera, D. Lavrenov (2021) Humanode whitepaper: You are [not] a bot. arXiv preprint arXiv:2111.13189
- Khare Rohit and Adam Rifkin (1997) Weaving a Web of Trust. World Wide Web Journal. Volume 2, Number 3, Pages 77–112.
- Lesaege, C., Ast, F., & George, W. (2019). Kleros Short Paper v1.0.7. https://kleros.io/static/whitepaper_en-8bd3a0480b45c39899787e17049ded26.pdf
- Giliani, Bertin, Hotin (2020) A Survey on Blockchain-based Identity Management and Decentralized Privacy for Personal Data/ https://hal.science/hal-02650705/file/BRAIN20_270520_Komal.pdf
- Nakamoto, S. (2008). Bitcoin: A peer-to-peer electronic cash system. Retrieved from https://bitcoin.org/bitcoin.pdf
- Rathee, T., & Singh, P. (2022). A systematic literature mapping on secure identity management using blockchain technology. Journal of King Saud University — Computer and Information Sciences, 34(8), 5782–5796. https://doi.org/10.1016/j.jksuci.2021.03.005
- Siddarth, D., Ivliev, S., Siri, S., & Berman, P. (2020). Who Watches the Watchmen? A Review of Subjective Approaches for Sybil-Resistance in Proof of Personhood Protocols. Frontiers in Blockchain. https://doi.org/10.3389/fbloc.2020.590171
- Schardong, F.; Custódio, R. Self-Sovereign Identity: A Systematic Review, Mapping and Taxonomy. Sensors 2022, 22, 5641. https://doi.org/10.3390/s22155641
- Swan, M. (2015). Blockchain: Blueprint for a new economy. O’Reilly Media, Inc.
- Turing, A. M. (1950). Computing machinery and intelligence. Mind, 59(236), 433–460.
- Von Ahn, L., Maurer, B., McMillen, C., Abraham, D., & Blum, M. (2008). reCAPTCHA: Human-Based Character Recognition via Web Security Measures. Science, 321(5895), 1465–1468.
- Zhiming Song, Guiwen Wang, Yimin Yu, Taowei Chen, “Digital Identity Verification and Management System of Blockchain-Based Verifiable Certificate with the Privacy Protection of Identity and Behavior”, Security and Communication Networks, vol. 2022, Article ID 6800938, 24 pages, 2022. https://doi.org/10.1155/2022/6800938

