Understanding the tech behind Humanode's Biometric Authentication process
Let’s cut to the chase: you’re probably wondering if Humanode’s Proof of Biometric Uniqueness is really as solid as we describe it. You’ve heard the pitch – biometrics over capital, privacy over profit— in our previous article Decentralization Through Biometric Uniqueness: One Person, One Node in Humanode.
But does it actually hold up when you dig into the technical details? And, most importantly, can your biometric data really stay private while securing a decentralized network?
It’s okay to feel a bit skeptical. Maybe you’re thinking, “How can biometric authentication keep a blockchain secure and protect my privacy?” You’re not alone—this kind of tech sounds almost too good to be true. But here’s the thing: Humanode didn’t just build a system that looks good on paper. The authentication, the the Do Not Trust But Verify architecture – it’s all designed to make sure your data stays locked down and never exposed.
Let’s walk through the technical details of Humanode’s bio-authentication system—step by step. We’ll dive into the code, the authentication processes, and how everything ties together to keep things both secure and private.
Let’s get started with the basics. But before that If you prefer watching the video instead of reading the article, here it is:
Node Launch Process
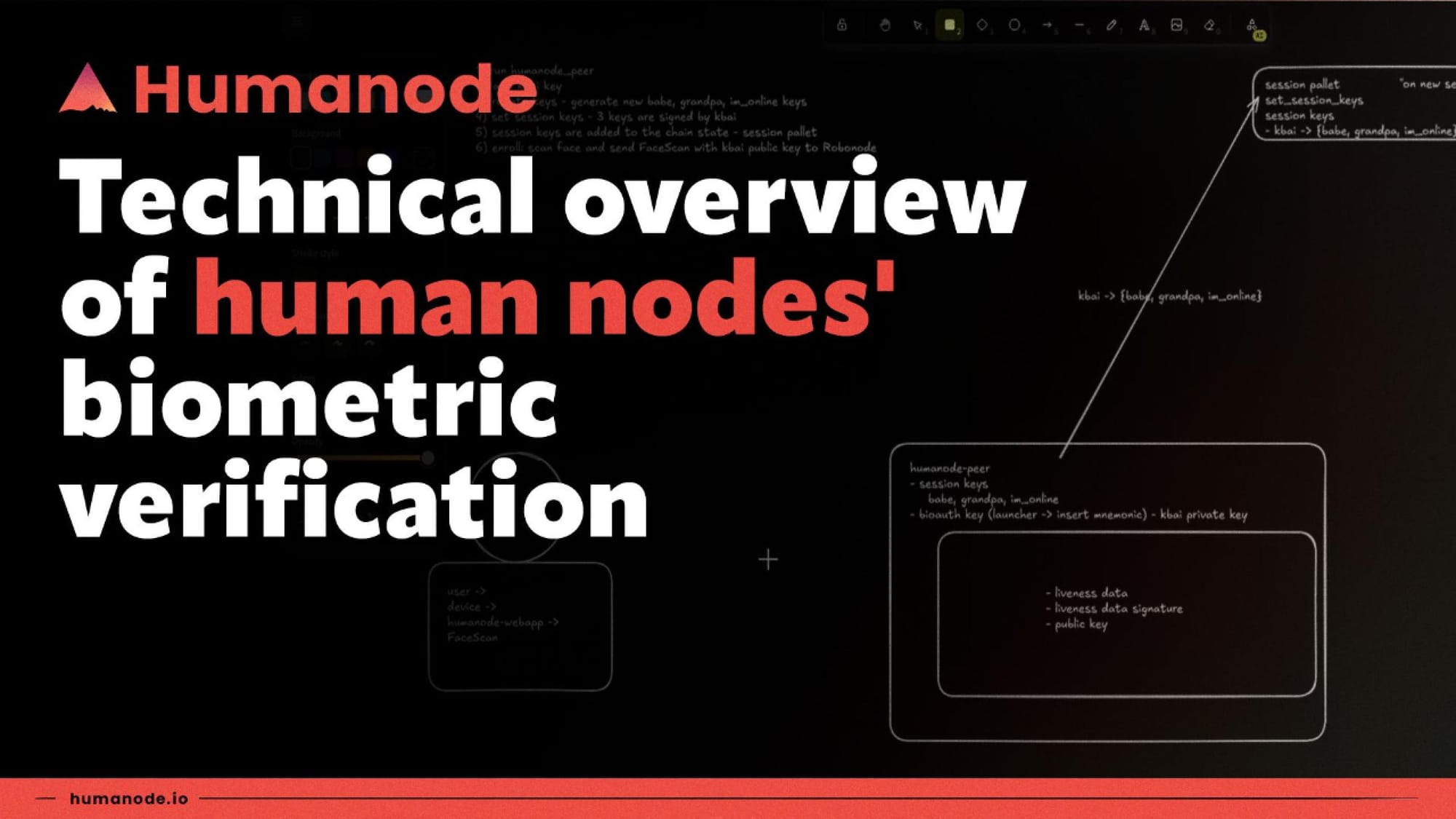
The first step in becoming a validator in the Humanode network is launching a Humanode-peer. Think of the peer as the software you need to run in order to join the network. It’s what makes your machine a “node” in the Humanode ecosystem.
Once you’ve launched the peer, it’s time to generate the keys that will authenticate your node and connect it to the network. The most important key here is your kbai key – your bioauth key. This key is tied to your biometrics and will be used not only to authenticate you as a unique human but also to perform validator logic related transactions, set up your node, and receive rewards.
But that’s not the only key in play. You’ll also generate three additional session keys:
babe key: This key is used for block production logic i.e. determining who gets to propose the next block.
grandpa key: This key is used for block finalization logic i.e. ensuring consensus across validators.
im_online key: It is used to signal that your node is online and ready to participate in the network.
After generating these keys, a special extrinsic set_key is created that lets you sign these keys with your kbai key and set them as your session keys by submitting the extrinsic to the network. At this point, you’re part of the network, but without biometric authentication, you’re not yet an active validator.
You can view the Humanode-peer source code in this Github repo.
Biometric Enrollment and Authentication Flow
This is where things get interesting. To prove that there’s a real, unique human behind your node, you need to go through biometric enrollment. This process is done through the Humanode WebApp, which connects directly to the node you just launched.
You can check Humanode-webapp source code in this repository.
Using the WebApp, you scan your face. The scan captures your unique biometric traits in 3D and runs liveness detection to confirm that you’re an actual living person—not a deepfake, a mask, or a video trick. The biometric data collected includes FaceMap and liveness data, all encrypted locally on your device.
From here, your encrypted FaceScan is sent to the Humanode-peer and processed through Robonode. This is where Confidential Virtual Machine (AMD-SEV-SNP) technology comes into play. Robonode ensures that all biometric computations happen in a secure, encrypted environment, meaning your sensitive biometric data is never exposed. Robonode compares your FaceScan to those already enrolled in the system to verify that you’re not already registered. Once confirmed, you’re ready to become an active validator.
Here’s how the whole process works:
Key Components
Let’s break down the key modules that keep this whole process running smoothly.
Session Pallet: Once your session keys are added, the Session Pallet tracks validator nodes over time. It’s responsible for forming the list of validators that will produce blocks and finalize them. Every four hours (an epoch), the Session Pallet refreshes, queuing up the next set of validators based on those who are actively authenticated.
Github repo for session pallet.
Bioauth Pallet: This is the part of the network responsible for managing your biometric authentication. After you’ve enrolled and been authenticated, your public key with the corresponding expiration timestamp (the time in which your bioauthentication will expire) is added to the list of activeAuthentications in the Bioauth Pallet. To get a better idea: A single bioauthentication expires in 168 hours or 42 epochs (one epoch is 4 hours).
But there’s more to it—since biometric validation isn’t permanent, the Bioauth Pallet regularly checks to ensure your authentication is still valid based on the current block timestamp and hasn’t expired, keeping the network secure and Sybil-resistant.
Robonode: The heart of Humanode’s privacy and security. Robonode is based on AMD-SEV-SNP technology and ensures that all biometric computations happen in an encrypted environment. No data leaves this secure domain in an unencrypted form. When your biometric data is processed, Robonode issues an auth_ticket, proving that you’ve been successfully authenticated. This ticket allows you to become an active validator.
Biometric Server: While Humanode ensures privacy through Robonode, it relies on FaceTec, for now, to provide the accuracy and security of its biometric scans. FaceTec’s software is responsible for verifying the liveness of the person scanning in. With over 60 modules working in tandem, FaceTec prevents fraud like deepfakes or injected video streams and ensures that the person behind the FaceScan is a real human being.
Once authenticated, your node is live, your identity verified, and you’re officially part of Humanode’s decentralized, human-driven network.
The Role of Robonode in Ensuring Privacy and Security
In a world where privacy concerns are at an all-time high, protecting sensitive biometric data is essential. Humanode takes this seriously, and the key to our system's privacy and security lies in Robonode.
Confidential Virtual Machines
So how does Robonode ensure your biometric data stays secure? It’s all about using Confidential Virtual Machines (CVMs). Specifically, Humanode employs AMD-SEV-SNP technology—the third generation of confidential computing. This might sound technical, but think of it like an ultra-secure vault. Every time biometric data is processed, Robonode locks that data inside this encrypted vault, where no prying eyes can access it.
Let’s break it down. When your FaceScan is taken, the data is immediately encrypted and sent to Robonode. But here’s the key: it’s not just encrypted in transit—it stays encrypted throughout the entire processing stage. At no point is your raw biometric data exposed to the system or to anyone involved in the process. Robonode client ensures that only encrypted biometric data enters the system, which means your privacy is guaranteed from start to finish.
Why is this important? Traditional systems often process sensitive data in a raw form, leaving it vulnerable to leaks or hacks. Robonode, however, makes sure this never happens. Every calculation, every comparison—everything happens behind the encrypted walls of the CVM, so you can rest assured that your personal information remains private.
Do Not Trust, Verify
Humanode doesn’t stop at encryption. We’ve adopted a Do Not Trust, Verify Approach, meaning that nothing in the system is automatically trusted. Every component, even the biometric server itself, must be continuously verified.
Let’s take an example: when the biometric server processes your FaceScan, it doesn’t get a free pass. Before anything is accepted by the network, Robonode checks that the server isn’t sending faulty or manipulated data. It’s a rigorous verification process that ensures no rogue components can interfere or introduce compromised data.
Essentially, Humanode operates on the belief that trust has to be earned every step of the way. This constant verification loop prevents bad actors from tampering with the biometric data or sneaking unauthorized data into the system. It’s like having a security guard at every door, checking credentials repeatedly—never assuming anything is safe just because it made it past the first checkpoint.
This Do Not Trust, Verify Approach creates a robust shield around the network, making sure no faulty data slips through the cracks. It’s one of the reasons Humanode can confidently handle sensitive biometric information while maintaining an unmatched level of security and privacy.
In short, Robonode ensures that even in a system built on biometric uniqueness, your personal data is never exposed. It’s all processed in a private, encrypted environment, with every action verified to make sure nothing goes unchecked. This is the future of secure, decentralized networks.
Validator Authentication and Session Handling
Once you’ve launched a node in Humanode, the journey doesn’t end there. To become an active validator, your node needs to go through a unique process of biometric authentication and session handling. Let’s break it down.
Becoming an Active Validator
To ensure there’s a real, unique human behind every node, you have to enroll and authenticate using biometrics. The process begins when you, the validator, scan your face using the Humanode WebApp. This isn’t just a quick selfie. The app captures a 3D FaceScan and runs liveness detection to confirm you’re a living person—not a deepfake, a video, or anything that could trick the system.
Once your biometric data is collected and encrypted, it’s sent to Humanode-peer, and from there it goes to Robonode. Robonode’s job is to keep that data safe and private while verifying if you’ve already enrolled or if you’re a new participant. In case you are a new participant and Robonode confirms that you’re not in the system, congratulations—you’re now on your way to becoming an active validator.
But you’re not quite there yet. Before you can officially join the validation process, Robonode generates something called an auth_ticket for authentication. Think of it as your golden ticket into the system. This auth_ticket contains your kbai public key (which ties you to your node) and a Robonode signature proving that you’ve been authenticated. Without this ticket, your node can’t participate in block production or validation.
Once you’ve got your auth_ticket, you send a special authentication transaction to the Humanode network. It’s important to remember that you have to reauthenticate every week or 168 hours to be exact, otherwise, your authentication is expired and you get removed from the validators list.
The network adds your public key and the expiration timestamp of your authentication to the bioauth pallet. Now, you’re a fully authenticated validator, ready to take part in the consensus process. The best part? Every validator, no matter their background or resources, gets equal weight in the network.
Session Pallet’s Role in Validator Rotation
Now that you’re authenticated, your node needs to be added to the validator queue. Here’s where the session pallet comes in.
The session pallet is responsible for forming the list of validators that will handle block production and finalization for a set period of time. This period, known as an epoch, lasts for 4 hours. At the end of each epoch, the session pallet rotates in new validators to ensure that validation is always being handled by unique and authenticated individuals.
Here’s how it works: once you’re authenticated, the bioauth pallet checks to ensure your authentication hasn’t expired. When a new session begins, the session pallet checks the bioauth pallet for a list of all validators with unexpired keys. Only those validators with active authentication are added to the next session’s queue. This ensures that only verified, unique individuals can participate in validation, reinforcing the “one person, one node” principle.
When the session ends, the session pallet refreshes the list of validators by running the on_new_session handler. This process kicks off another cycle, and if your keys are still valid, you’re added back into the pool of active validators. It’s a seamless rotation designed to keep the network decentralized and secure, without any gaps in validation.
This constant shuffling of validators, every four hours, guarantees that the network isn’t controlled by a static group of participants. Instead, the system ensures that the power of validation is continuously redistributed among unique, verified individuals. It’s a dynamic, fair process that protects the network from consolidation and ensures continuous participation from across the globe.
Humanode’s system of validator authentication and session handling flips the script on traditional blockchain models. No more mining pools or staking powerhouses. Just real people, authenticated biometrically, taking turns to ensure the network remains truly decentralized and secure.
The Benefits of Proof of Biometric Uniqueness
The magic of Humanode’s consensus mechanism isn’t just in how it works—it’s in why it works. By breaking away from traditional blockchain models, Humanode delivers something different: fairness, security, and privacy. Let’s explore what makes this approach so unique.
True Decentralization
In most blockchains, decentralization is a promise that’s hard to fully deliver. Power tends to gather in the hands of the wealthy, whether it’s miners with expensive hardware in PoW systems or the wealthiest stakers in PoS networks. Humanode throws that old formula out the window.
At the heart of Humanode’s system is a radical idea: one person, one node, one vote. No matter who you are or how much capital you have, your influence in the network is exactly equal to everyone else’s. There are no mining pools to overpower you, no stakers with massive holdings to drown out your vote. It’s true decentralization, driven by human uniqueness, not wealth.
This breaks the cycle we see in traditional systems where those with resources gain control, and the rest of us just follow. Here, each validator holds the same weight. It doesn’t matter if you’re a tech giant or an individual at home—your node has the same influence as the next person’s. This is decentralization as it was always meant to be: fair, balanced, and built on the equality of all participants.
Sybil-Resistance
Sybil attacks, where an attacker floods the network with fake identities to gain control, are a nightmare for decentralized systems. The more fake nodes they control, the more influence they have, and the easier it becomes to manipulate consensus.
Humanode addresses this problem at its core. By requiring private biometric verification, Humanode ensures that each node is tied to a real, unique human being. This means no one can spin up multiple nodes using fake identities or extra capital. The system is practically immune to Sybil attacks because, at its foundation, every validator is a verified individual. Even if someone wanted to game the system, they’d need to create multiple human identities—and that’s not happening.
In most systems, money acts as the barrier to prevent Sybil attacks. But money can be amassed. Human identity, on the other hand, is unique. By tying validation to the identity of a living person, Humanode creates a defense against Sybil attacks that’s stronger than any financial requirement.
Privacy-Centric
Now, you might be wondering: But what about privacy? After all, biometric data is personal, sensitive information. Humanode understands this and goes to great lengths to protect it.
Everything starts with cryptobiometrics. Your biometric data—whether it’s your face or another unique identifier—is never stored in its raw form. As soon as your face is scanned, it’s converted into an encrypted format and securely processed through Robonode’s Confidential Virtual Machines (CVMs). This ensures that not only is your data protected during transmission, but it remains encrypted throughout the entire process.
Here’s the key point: your personal information stays with you. The raw biometric data never leaves your device. What gets processed on the network is an encrypted version that can’t be traced back to you. Even as you participate in validation and consensus, your privacy remains intact.
It’s a rare combination in the world of blockchain: a system that’s both secure and private. Most networks struggle to balance privacy with transparency, but Humanode’s use of confidential computing and Do Not Trust, Verify architecture makes sure your identity is verified without ever being exposed.
Summing Up
Humanode has built a powerful foundation with its PoBU, but this is just the beginning. The system’s design opens up a world of possibilities, from expanding biometric modalities to scaling the network globally.
Expanding Beyond Facial Recognition
Currently, Humanode relies on facial recognition as the biometric backbone of its consensus mechanism. But that’s not where it ends. The potential to integrate other biometric modalities—like fingerprint, palm, or iris recognition—is on the horizon. Imagine a future where validators can use a variety of unique human traits to authenticate themselves.
Palm recognition is a particularly exciting option. The unique patterns of veins in your palm can be scanned and used as a secure biometric identifier. This method is non-intrusive and highly accurate, often used in industries where security is paramount. Palm recognition, like fingerprints, is hard to replicate, making it a natural fit for Humanode’s privacy-focused system.
Iris recognition also brings another level of precision, often considered one of the most reliable biometric methods due to the complexity of iris patterns. By incorporating multiple modalities, Humanode can cater to various devices and regions, ensuring the network remains inclusive without sacrificing security.
By allowing these multiple modalities, Humanode not only strengthens its biometric security but also provides users with flexibility, making participation more accessible across different platforms and environments.
Scalability and Global Adoption
As Humanode continues to grow, the question of scalability becomes crucial. Can the network handle thousands—or even millions—of unique validators without breaking a sweat? The short answer is yes.
Humanode’s system is designed in a way that we can change the consensus algorithm while staying with the same validator set and the same consensus mechanism. The combination of biometric authentication and confidential computing allows it to accommodate a growing number of validators without compromising security or speed. As more people around the world join the network, each one bringing their unique biometric identity, the system strengthens, ensuring decentralization remains intact.
The key here is that Humanode’s approach isn’t just about adding more validators. It’s about expanding globally in a way that’s sustainable. By incorporating liveness detection and cryptobiometrics, Humanode guarantees that every new participant is a real human—no matter how big the network gets. Whether it’s 1,000 validators or 1,000,000, the principles of equality and Sybil-resistance remain untouched.
Integration with Other Layer 1 and Layer 2 chains
Humanode isn’t an isolated system. Thanks to its EVM compatibility, it opens the door to a world of decentralized applications and use cases. For developers, this means you can build on top of Humanode just as you would on any Ethereum-compatible network, but with the added security and decentralization that comes from biometric uniqueness.
Imagine integrating Humanode’s consensus mechanism into other Layer 1 and Layer 2 systems. This could allow for biometric-based authentication in a variety of dApps, from DeFi to gaming, with each participant securely verified as a unique human. In decentralized finance, this could mean real democracy in governance, where financial control isn’t based on who holds the most tokens but on human participation. In gaming, it could prevent bot-fueled economies, ensuring that each player is a real person, contributing to a fairer ecosystem.
The possibilities are vast. Humanode’s compatibility with other systems makes it a perfect layer to enhance security and decentralization in a wide range of applications.

