Sybil-resistant airdrops with Humanode BotBasher

A specific occurrence exclusive to the crypto world airdrops provide a unique opportunity to engage with the community and reward loyal supporters.
An airdrop is a promotional activity where the protocols and projects grant a series of tokens to their early supporters after launching native tokens. This move is mainly aimed at getting traction and attracting users who will trade in when the project gets listed on exchanges.
For those new to the idea, it might be surprising to learn that some airdrops can grant recipients tokens of significant value, sometimes worth thousands of dollars or more.
While the days of airdrops leading to immense wealth have dipped and flowed over time, the phenomenon has recently experienced a resurgence thanks to protocols such as Optimism, Aptos, and Arbitrum.
Sybil attacks on airdrops
Although airdrops provide a unique opportunity for these projects to reward loyal supporters, malicious actors known as "airdrop hunters" often exploit these airdrops. And the result is a plunge in the token’s value.
A Sybil attack occurs when an individual or group creates multiple accounts or uses bots to manipulate a system for personal gain. In the context of airdrops, airdrop hunters utilize multi accounts, bots, and even fake social media profiles to increase their share of the distributed tokens.
For instance, a CoinDesk article recently featured an anonymous airdrop hunter who professed to have accumulated considerable wealth by Sybil attacking airdrops. This individual even alleged that acquaintances made millions of dollars solely from the Arbitrum airdrop. This and many other such exploitation incidents of Arbitrum airdrop have been the talk of the town nowadays.
Similarly, the price of Optimism’s token plummeted by more than 65% soon after its launch as roughly 17,000 wallets that claimed the airdrop immediately dumped their OP tokens for profits.
And it is not an Arbitrum or Optimism-only problem; numerous cases have been reported within the crypto industry of airdrop hunters using multiple accounts and bots to maliciously acquire tokens worth hundreds or even millions of dollars and selling them shortly.
The farming networks involved in these activities are highly advanced and robust, making it incredibly difficult to trace and penalize them. In all honesty, many protocols and networks do not have a system to stop it from occurring. Here is a graphical representation of one of the Sybil attacks identified by Alchemy.
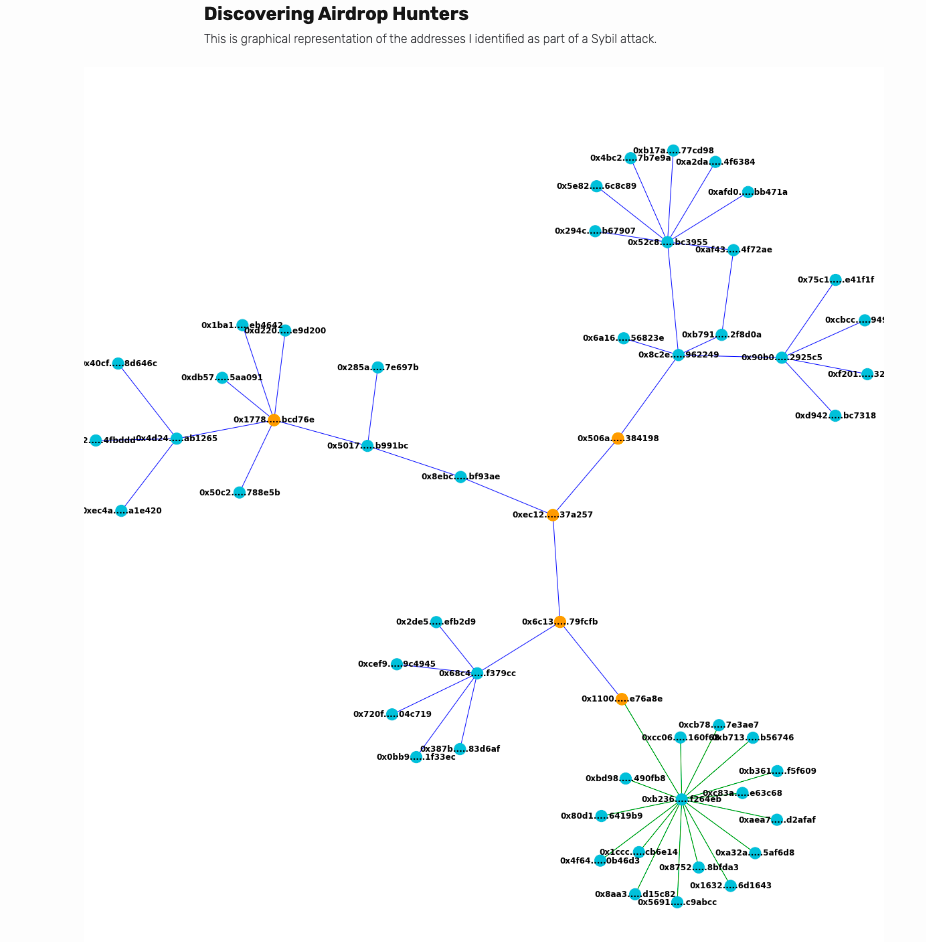
You can see a pattern of how sophistically four major addresses accumulated tokens using all other addresses.
These kinds of attacks not only compromise the integrity of a project but also detract from the core objectives of airdrops i.e.
- Encouraging community growth
- Rewarding loyal supporters
When a project falls victim to Sybil attacks orchestrated by hunters, neither of these goals is achieved. It might appear that your project has gained significant traction, but this perception is misleading. Particularly, if you aim for long-term success, the project ultimately suffers setbacks.
Sybil attacks on airdrops can result in a variety of problems for your project:
- Short-selling by airdrop hunters: When airdrop hunters obtain a large portion of the distributed tokens, they may engage in short-selling once these tokens become tradable. This action can generate downward price pressure, deterring long-term investors from participating.
- No allocation to genuine members: If airdrop hunters manage to seize a considerable share of the distributed tokens, legitimate supporters could be left empty-handed. This outcome can cause dissatisfaction and even lead to members leaving the community.
So, you might be wondering what's the big deal? Why are we talking so much about Sybil's attacks on airdrops? If they're that bad, why haven't we found a solution yet? How can we counter these attacks? I know you've got a lot of questions brewing in your curious mind, so let me break it down for you.
Sybil attacks on airdrops aren't a new thing; they've been around for as long as airdrops themselves. And there have been proposed solutions to tackle these issues. For instance, the CoinDesk report and the Alchemy article I mentioned earlier, offered ideas to track down airdrop hunters.
The problem with these solutions is that they try to catch the attackers after they've successfully intruded and gathered the tokens, which is hard, even impossible in most cases.
But what if there’s a way to put up a barrier to stop attackers from entering the system and causing trouble?
BotBasher: A sybil-resistant approach to airdrop distribution
This is where Humanode tech integrated with Discord - BotBasher plays a major role. To utilize its capabilities, simply add BotBasher to your Discord server alongside any bot that gets users’ wallet addresses. Then, create sybil-resistant channels allocated for the airdrops, accessible only by verified humans, and invite your community members to obtain a verified role.
Consequently, they can access the Sybil-resistant channel, register their wallets, and perform the assigned tasks to qualify for airdrops. If this seems confusing, don't worry—a detailed guide is provided at the end of this article. First, let's explore how BotBasher ensures Sybil resistance in your airdrops.
Basically, BotBasher is a Discord application built using Humanode's private biometric verification technology. This technology enables Discord users to confirm that their account is operated by a unique, living person. Discord servers can establish Sybil-resistant channels by granting access only to verified human users.
Using BotBasher, community members can get a verified role by going through a 15 seconds facial recognition session which proves that they are unique and living human beings. After successful completion, they can get access to the Sybil-resistant channels allocated for airdrops.
While reading about facial recognition might create multiple doubts in your mind about the security of BotBasher and the privacy of the users, it’s nothing actually to worry about. In short, the only data that anyone could get their hands on (if they are lucky enough) is a Discord ID tied with a random string. No personally identifiable information is either collected from users or stored on the servers or anywhere else.
With BotBasher and a suitable bot to gather wallet addresses, projects can ensure that airdrops are safe from sybil attacks that have been haunting us for a long time.
Integrating BotBasher to your Discord server is as easy as ABC. There’s no coding involved.
How to add BotBasher to your Discord?
Here’s how you can set up BotBasher on your server:
1. Install BotBasher on your server and create a new role that will be allocated to the verified humans only.
Here’s a step-by-step guide on how to install BotBasher on your Discord server.
2. Create new channel(s) / or set old ones such that they will only be accessed by verified humans.
3. Ask the community members to get a verified role. Members can refer to this guide to get a verified role. Or simply follow the steps mentioned here.
4. Add a suitable bot to gather users’ wallet addresses to become eligible for airdrops and configure the bot to grant access for it to be used in Sybil-resistant channels only by verified humans. Here’s a popular whitelisting bot.

5. Conduct Sybil-resistant airdrops in your Discord server!
BotBasher makes it easier for Discord servers to not only conduct sybil-resistant airdrops but to perform various activities such as 1 person 1 vote polling, Sybil-resistant whitelisting, Sybil resistant NFT-minting, contests, and much more.
Give BotBasher a try for free – https://botbasher.humanode.io/

